记录
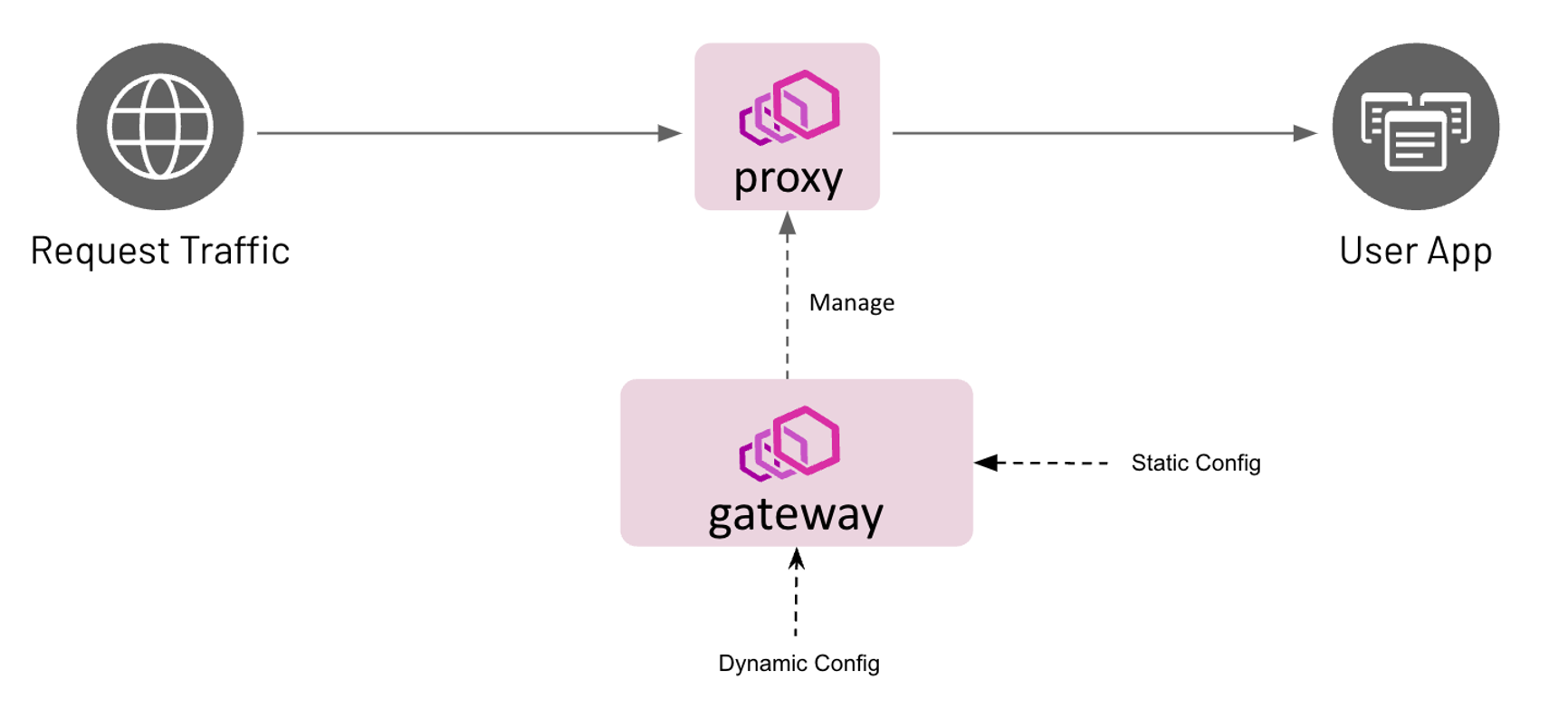
该项目正在积极开发中,很多功能尚待补充,我们希望您参与其中!Envoy Gateway 是一个开源项目,用于将 Envoy Proxy 作为独立或基于 Kubernetes 的应用程序网关进行管理。 Gateway API 资源用于动态供应和配置托管 Envoy 代理。
This is the multi-page printable view of this section. Click here to print.
Envoy Gateway 是一个开源项目,用于将 Envoy Proxy 作为独立或基于 Kubernetes 的应用程序网关进行管理。 Gateway API 资源用于动态供应和配置托管 Envoy 代理。

本指南将帮助您通过几个简单的步骤开始使用 Envoy Gateway。
一个 Kubernetes 集群。
注意: 请参考兼容性表格来查看所支持的 Kubernetes 版本。
注意: 如果您的 Kubernetes 集群没有负载均衡器实现,我们建议安装一个 ,以便 Gateway 资源能够关联一个地址。我们推荐使用 MetalLB。
安装 Gateway API CRD 和 Envoy Gateway:
helm install eg oci://docker.io/envoyproxy/gateway-helm --version v0.0.0-latest -n envoy-gateway-system --create-namespace
等待 Envoy Gateway 至可用后:
kubectl wait --timeout=5m -n envoy-gateway-system deployment/envoy-gateway --for=condition=Available
安装 GatewayClass,Gateway,HTTPRoute 和示例应用:
kubectl apply -f https://github.com/envoyproxy/gateway/releases/download/latest/quickstart.yaml -n default
注意:quickstart.yaml 定义了 Envoy Gateway 将侦听其全局可路由 IP 地址上端口
80 上的流量,以便轻松使用浏览器测试 Envoy Gateway。当 Envoy Gateway 看到它的侦听器使用特权端口(<1024),
它将在内部映射到非特权端口,因此 Envoy Gateway 不需要额外的特权。
了解此映射很重要,当您调试时您可能需要将其考虑在内。
获取由示例 Gateway 创建的 Envoy 服务的名称:
export ENVOY_SERVICE=$(kubectl get svc -n envoy-gateway-system --selector=gateway.envoyproxy.io/owning-gateway-namespace=default,gateway.envoyproxy.io/owning-gateway-name=eg -o jsonpath='{.items[0].metadata.name}')
端口转发到 Envoy 服务:
kubectl -n envoy-gateway-system port-forward service/${ENVOY_SERVICE} 8888:80 &
通过 Envoy 代理,使用 curl 测试示例应用:
curl --verbose --header "Host: www.example.com" http://localhost:8888/get
您还可以通过将流量发送到外部 IP 来测试相同的功能。运行下面的命令可以获取 Envoy 服务的外部 IP 地址:
export GATEWAY_HOST=$(kubectl get svc/${ENVOY_SERVICE} -n envoy-gateway-system -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
在某些环境中,负载均衡器可能会公开主机名而不是 IP 地址,如果是这样,将上述命令中的 ip 替换为 hostname 。
使用 curl 来通过 Envoy Proxy 访问示例应用:
curl --verbose --header "Host: www.example.com" http://$GATEWAY_HOST/get
在快速开始(本节),您将:
以下是建议的后续任务列表,可指导您探索 Envoy Gateway:
请查看与您使用情况相符的场景下的任务部分。Envoy Gateway 的任务按照流量管理、安全、扩展性、可观察性和运维等分类组织。
请按照本节中的步骤将快速入门中的所有内容卸载。
删除 GatewayClass,Gateway,HTTPRoute 和示例应用:
kubectl delete -f https://github.com/envoyproxy/gateway/releases/download/latest/quickstart.yaml --ignore-not-found=true
删除 Gateway API CRD 和 Envoy Gateway:
helm uninstall eg -n envoy-gateway-system
浏览开发者指南 ,了解如何参与项目。
GRPCRoute 资源允许用户通过匹配 HTTP/2 流量并将其转发到后端 gRPC 服务器来配置 gRPC 路由。 要了解有关 gRPC 路由的更多信息,请参阅Gateway API 文档。
按照快速入门中的步骤安装 Envoy Gateway 和示例清单。 在继续之前,您应该能够使用 HTTP 查询示例程序后端。
安装 gRPC 路由示例资源:
kubectl apply -f https://raw.githubusercontent.com/envoyproxy/gateway/latest/examples/kubernetes/grpc-routing.yaml
该清单安装 GatewayClass、Gateway、Deployment、Service 和 GRPCRoute 资源。 GatewayClass 是集群范围的资源,表示可以被实例化的一类 Gateway。
**注意:**Envoy Gateway 默认被配置为使用 controllerName: gateway.envoyproxy.io/gatewayclass-controller 管理 GatewayClass。
检查 GatewayClass 的状态:
kubectl get gc --selector=example=grpc-routing
状态应反映为 Accepted=True,表示 Envoy Gateway 正在管理 GatewayClass。
Gateway 代表基础设施的配置。创建 Gateway 时,Envoy 代理基础设施由 Envoy Gateway 预配或配置。
gatewayClassName 定义此 Gateway 使用的 GatewayClass 的名称。检查 Gateway 状态:
kubectl get gateways --selector=example=grpc-routing
状态应反映为 Ready=True,表示 Envoy 代理基础设施已被配置。
该状态还提供 Gateway 的地址。该地址稍后用于测试与代理后端服务的连接。
检查 GRPCRoute 的状态:
kubectl get grpcroutes --selector=example=grpc-routing -o yaml
GRPCRoute 的状态应显示 Accepted=True 和引用示例 Gateway 的 parentRef。
example-route 匹配 grpc-example.com 的任何流量并将其转发到 yages 服务。
在测试到 yages 后端的 GRPC 路由之前,请获取 Gateway 的地址。
export GATEWAY_HOST=$(kubectl get gateway/example-gateway -o jsonpath='{.status.addresses[0].value}')
使用 grpcurl 命令测试到 yages 后端的 GRPC 路由。
grpcurl -plaintext -authority=grpc-example.com ${GATEWAY_HOST}:80 yages.Echo/Ping
您应该看到以下响应:
{
"text": "pong"
}
Envoy Gateway 还支持此配置的 gRPC-Web 请求。下面的 curl 命令可用于通过 HTTP/2 发送 grpc-Web 请求。
您应该收到与上一个命令相同的响应。
正文 AAAAAAA= 中的数据是 Ping RPC 接受的空消息(数据长度为 0)的 Base64 编码表示。
curl --http2-prior-knowledge -s ${GATEWAY_HOST}:80/yages.Echo/Ping -H 'Host: grpc-example.com' -H 'Content-Type: application/grpc-web-text' -H 'Accept: application/grpc-web-text' -XPOST -d'AAAAAAA=' | base64 -d
matches 字段可用于根据 GRPC 的服务和/或方法名称将路由限制到一组特定的请求。
它支持两种匹配类型:Exact(精准)和 RegularExpression(正则)。
Exact(精准)匹配是默认匹配类型。
以下示例显示如何根据 grpc.reflection.v1alpha.ServerReflection/ServerReflectionInfo 的服务和方法名称来匹配请求,
以及如何在我们的部署中匹配方法名称为 Ping 且与 yages.Echo/Ping 匹配的所有服务。
cat <<EOF | kubectl apply -f -
apiVersion: gateway.networking.k8s.io/v1alpha2
kind: GRPCRoute
metadata:
name: yages
labels:
example: grpc-routing
spec:
parentRefs:
- name: example-gateway
hostnames:
- "grpc-example.com"
rules:
- matches:
- method:
method: ServerReflectionInfo
service: grpc.reflection.v1alpha.ServerReflection
- method:
method: Ping
backendRefs:
- group: ""
kind: Service
name: yages
port: 9000
weight: 1
EOF
保存以下资源并将其应用到您的集群:
---
apiVersion: gateway.networking.k8s.io/v1alpha2
kind: GRPCRoute
metadata:
name: yages
labels:
example: grpc-routing
spec:
parentRefs:
- name: example-gateway
hostnames:
- "grpc-example.com"
rules:
- matches:
- method:
method: ServerReflectionInfo
service: grpc.reflection.v1alpha.ServerReflection
- method:
method: Ping
backendRefs:
- group: ""
kind: Service
name: yages
port: 9000
weight: 1
验证 GRPCRoute 状态:
kubectl get grpcroutes --selector=example=grpc-routing -o yaml
使用 grpcurl 命令测试到 yages 后端的 GRPC 路由。
grpcurl -plaintext -authority=grpc-example.com ${GATEWAY_HOST}:80 yages.Echo/Ping
以下示例演示如何根据服务和方法名称将请求与匹配类型 RegularExpression 进行匹配。
它与模式 /.*.Echo/Pin.+ 匹配所有服务和方法,该模式与我们部署中的 yages.Echo/Ping 匹配。
cat <<EOF | kubectl apply -f -
apiVersion: gateway.networking.k8s.io/v1alpha2
kind: GRPCRoute
metadata:
name: yages
labels:
example: grpc-routing
spec:
parentRefs:
- name: example-gateway
hostnames:
- "grpc-example.com"
rules:
- matches:
- method:
method: ServerReflectionInfo
service: grpc.reflection.v1alpha.ServerReflection
- method:
method: "Pin.+"
service: ".*.Echo"
type: RegularExpression
backendRefs:
- group: ""
kind: Service
name: yages
port: 9000
weight: 1
EOF
保存以下资源并将其应用到您的集群:
---
apiVersion: gateway.networking.k8s.io/v1alpha2
kind: GRPCRoute
metadata:
name: yages
labels:
example: grpc-routing
spec:
parentRefs:
- name: example-gateway
hostnames:
- "grpc-example.com"
rules:
- matches:
- method:
method: ServerReflectionInfo
service: grpc.reflection.v1alpha.ServerReflection
- method:
method: "Pin.+"
service: ".*.Echo"
type: RegularExpression
backendRefs:
- group: ""
kind: Service
name: yages
port: 9000
weight: 1
检查 GRPCRoute 状态:
kubectl get grpcroutes --selector=example=grpc-routing -o yaml
使用 grpcurl 命令测试到 yages 后端的 GRPC 路由。
grpcurl -plaintext -authority=grpc-example.com ${GATEWAY_HOST}:80 yages.Echo/Ping
此任务提供有关配置 JSON Web Token(JWT)身份验证的说明。
JWT 身份验证在将请求路由到后端服务之前检查传入请求是否具有有效的 JWT。
目前,Envoy Gateway 仅支持通过 HTTP 标头验证 JWT,例如 Authorization: Bearer <token>。
Envoy Gateway 引入了一个名为 SecurityPolicy 的新 CRD,允许用户配置 JWT 身份验证。 该实例化资源可以链接到 Gateway、HTTPRoute 或 GRPCRoute 资源。
按照快速入门中的步骤安装 Envoy Gateway 和示例清单。 对于 GRPC - 请按照 GRPC 路由示例中的步骤操作。 在继续之前,您应该能够使用 HTTP 或 GRPC 查询示例程序后端。
通过创建 SecurityPolicy 并将其附加到示例 HTTPRoute 或 GRPCRoute,允许使用具有有效 JWT 的请求。
kubectl apply -f https://raw.githubusercontent.com/envoyproxy/gateway/latest/examples/kubernetes/jwt/jwt.yaml
已创建两个 HTTPRoute,一个用于 /foo,另一个用于 /bar。
已创建 SecurityPolicy 并以 HTTPRoute foo 为目标来验证对 /foo 的请求。
HTTPRoute bar 不是 SecurityPolicy 的目标,并且将允许未经身份验证的请求发送到 /bar。
验证 HTTPRoute 配置和状态:
kubectl get httproute/foo -o yaml
kubectl get httproute/bar -o yaml
SecurityPolicy 配置为 JWT 身份验证,并使用单个 JSON Web Key Set(JWKS)提供程序来对 JWT 进行身份验证。
验证 SecurityPolicy 配置:
kubectl get securitypolicy/jwt-example -o yaml
kubectl apply -f https://raw.githubusercontent.com/envoyproxy/gateway/latest/examples/kubernetes/jwt/grpc-jwt.yaml
已创建 SecurityPolicy 并针对 GRPCRoute yages 来验证 yages 服务的所有请求。
验证 GRPCRoute 配置和状态:
kubectl get grpcroute/yages -o yaml
SecurityPolicy 配置为 JWT 身份验证,并使用单个 JSON Web Key Set(JWKS)提供程序来对 JWT 进行身份验证。
验证 SecurityPolicy 配置:
kubectl get securitypolicy/jwt-example -o yaml
确保设置了快速入门 中的 GATEWAY_HOST 环境变量。如果没有,请按照快速入门说明设置变量。
echo $GATEWAY_HOST
验证在没有 JWT 的情况下对 /foo 的请求是否被拒绝:
curl -sS -o /dev/null -H "Host: www.example.com" -w "%{http_code}\n" http://$GATEWAY_HOST/foo
应返回一个 401 HTTP 响应码。
获取用于测试请求身份验证的 JWT:
TOKEN=$(curl https://raw.githubusercontent.com/envoyproxy/gateway/main/examples/kubernetes/jwt/test.jwt -s) && echo "$TOKEN" | cut -d '.' -f2 - | base64 --decode
**注意:**上述命令解码并返回令牌的有效内容。您可以将 f2 替换为 f1 来查看令牌的标头。
验证是否允许使用有效 JWT 向 /foo 发出请求:
curl -sS -o /dev/null -H "Host: www.example.com" -H "Authorization: Bearer $TOKEN" -w "%{http_code}\n" http://$GATEWAY_HOST/foo
应返回一个 200 HTTP 响应码。
验证是否允许在没有 JWT 的情况下向 /bar 发出请求:
curl -sS -o /dev/null -H "Host: www.example.com" -w "%{http_code}\n" http://$GATEWAY_HOST/bar
验证是否在没有 JWT 的情况下拒绝对 yages 服务的请求:
grpcurl -plaintext -authority=grpc-example.com ${GATEWAY_HOST}:80 yages.Echo/Ping
您应该看到以下响应:
Error invoking method "yages.Echo/Ping": rpc error: code = Unauthenticated desc = failed to query for service descriptor "yages.Echo": Jwt is missing
获取用于测试请求身份验证的 JWT:
TOKEN=$(curl https://raw.githubusercontent.com/envoyproxy/gateway/main/examples/kubernetes/jwt/test.jwt -s) && echo "$TOKEN" | cut -d '.' -f2 - | base64 --decode
**注意:**上述命令解码并返回令牌的有效内容。您可以将 f2 替换为 f1 来查看令牌的标头。
验证是否允许使用有效 JWT 向 yages 服务发出请求:
grpcurl -plaintext -H "authorization: Bearer $TOKEN" -authority=grpc-example.com ${GATEWAY_HOST}:80 yages.Echo/Ping
您应该看到以下响应:
{
"text": "pong"
}
按照快速入门 中的步骤卸载 Envoy Gateway 和示例清单。
删除 SecurityPolicy:
kubectl delete securitypolicy/jwt-example
查看开发者指南参与该项目。
Helm 是 Kubernetes 的包管理器,可自动在 Kubernetes 上发布和管理软件。
Envoy Gateway 可以通过 Helm Chart 经过几个简单的步骤进行安装, 具体取决于您是首次部署、从现有安装升级 Envoy Gateway 还是从 Envoy Gateway 迁移。
Envoy Gateway Helm Chart 托管在 DockerHub 中。
它发布在 oci://docker.io/envoyproxy/gateway-helm。
Envoy Gateway 通常从命令行部署到 Kubernetes。如果您没有 Kubernetes,则应该使用 kind 来创建一个。
安装 Gateway API CRD 和 Envoy Gateway:
helm install eg oci://docker.io/envoyproxy/gateway-helm --version v0.0.0-latest -n envoy-gateway-system --create-namespace
等待 Envoy Gateway 变为可用:
kubectl wait --timeout=5m -n envoy-gateway-system deployment/envoy-gateway --for=condition=Available
安装 GatewayClass、Gateway、HTTPRoute 和示例应用程序:
kubectl apply -f https://github.com/envoyproxy/gateway/releases/download/latest/quickstart.yaml -n default
注意:quickstart.yaml 定义 Envoy Gateway 将侦听 80 端口及其全局可路由 IP 地址的流量,
以便轻松使用浏览器测试 Envoy Gateway。当 Envoy Gateway 发现其侦听器正在使用特权端口(<1024)时,
它会在内部将其映射到非特权端口,以便 Envoy Gateway 不需要额外的特权。了解此映射很重要,因为您在调试时可能需要考虑它。
下面是使用 helm install 命令进行 Envoy Gateway 安装的一些快速方法。
helm install eg oci://docker.io/envoyproxy/gateway-helm --version v0.0.0-latest -n envoy-gateway-system --create-namespace --set deployment.replicas=2
如果您使用不同的域名安装了集群,则可以使用以下命令。
helm install eg oci://docker.io/envoyproxy/gateway-helm --version v0.0.0-latest -n envoy-gateway-system --create-namespace --set kubernetesClusterDomain=<domain name>
**注意:**以上是我们可以直接用于自定义安装的一些方法。但如果您正在寻找更复杂的更改, values.yaml 可以帮助您。
deployment:
envoyGateway:
resources:
limits:
cpu: 700m
memory: 128Mi
requests:
cpu: 10m
memory: 64Mi
ports:
- name: grpc
port: 18005
targetPort: 18000
- name: ratelimit
port: 18006
targetPort: 18001
config:
envoyGateway:
logging:
level:
default: debug
在这里,我们对 value.yaml 文件进行了三处更改。将 CPU 的资源限制增加到 700m,
将 gRPC 的端口更改为 18005,将限流端口更改为 18006,并将日志记录级别更新为 debug。
您可以通过以下命令使用 value.yaml 文件安装 Envoy Gateway。
helm install eg oci://docker.io/envoyproxy/gateway-helm --version v0.0.0-latest -n envoy-gateway-system --create-namespace -f values.yaml
这些是 Envoy Gateway 和托管 Envoy 代理使用的端口。
| Envoy Gateway | 地址 | 端口 | 是否可配置 |
|---|---|---|---|
| Xds EnvoyProxy Server | 0.0.0.0 | 18000 | No |
| Xds RateLimit Server | 0.0.0.0 | 18001 | No |
| Admin Server | 127.0.0.1 | 19000 | Yes |
| Metrics Server | 0.0.0.0 | 19001 | No |
| Health Check | 127.0.0.1 | 8081 | No |
| Envoy Proxy | 地址 | 端口 |
|---|---|---|
| Admin Server | 127.0.0.1 | 19000 |
| Heath Check | 0.0.0.0 | 19001 |
此任务将引导您完成在 Kubernetes 集群中安装 Envoy Gateway。
手动安装过程不允许像 Helm 安装方法那样对配置进行更多控制, 因此如果您需要对 Envoy Gateway 安装进行更多控制,建议您使用 Helm。
Envoy Gateway 设计为在 Kubernetes 中运行以进行生产。最重要的要求是:
kubectl 命令行工具Envoy Gateway 通常从命令行部署到 Kubernetes。如果您没有 Kubernetes,则应该使用 kind 来创建一个。
在终端中,运行以下命令:
kubectl apply -f https://github.com/envoyproxy/gateway/releases/download/latest/install.yaml
后续步骤
Envoy Gateway 现在应该已成功安装并运行,但是为了体验 Envoy Gateway 的更多功能,您可以参考任务。
Envoy Gateway 为 Envoy Gateway Pod 和 Envoy 代理队列之间的控制平面通信建立了安全的 TLS 连接。 此处使用的 TLS 证书是自签名的,并使用在创建 Envoy Gateway 之前运行的 Job 生成, 并且这些证书被安装到 Envoy Gateway 和 Envoy 代理 Pod 上。
此任务将引导您完成为控制平面身份验证配置自定义证书。
我们使用 Cert-Manager 来管理证书。 您可以按照官方指南安装它。
首先您需要设置 CA 颁发者,在此任务中,我们以 selfsigned-issuer 为例。
您不应在生产中使用自签名颁发者,您应该使用真实的 CA 颁发者。
cat <<EOF | kubectl apply -f -
apiVersion: cert-manager.io/v1
kind: Issuer
metadata:
labels:
app.kubernetes.io/name: envoy-gateway
name: selfsigned-issuer
namespace: envoy-gateway-system
spec:
selfSigned: {}
---
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
name: envoy-gateway-ca
namespace: envoy-gateway-system
spec:
isCA: true
commonName: envoy-gateway
secretName: envoy-gateway-ca
privateKey:
algorithm: RSA
size: 2048
issuerRef:
name: selfsigned-issuer
kind: Issuer
group: cert-manager.io
---
apiVersion: cert-manager.io/v1
kind: Issuer
metadata:
labels:
app.kubernetes.io/name: envoy-gateway
name: eg-issuer
namespace: envoy-gateway-system
spec:
ca:
secretName: envoy-gateway-ca
EOF
为 Envoy Gateway 控制器创建一个证书,该证书将存储在 envoy-gatewy Secret 中。
cat<<EOF | kubectl apply -f -
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
labels:
app.kubernetes.io/name: envoy-gateway
name: envoy-gateway
namespace: envoy-gateway-system
spec:
commonName: envoy-gateway
dnsNames:
- "envoy-gateway"
- "envoy-gateway.envoy-gateway-system"
- "envoy-gateway.envoy-gateway-system.svc"
- "envoy-gateway.envoy-gateway-system.svc.cluster.local"
issuerRef:
kind: Issuer
name: eg-issuer
usages:
- "digital signature"
- "data encipherment"
- "key encipherment"
- "content commitment"
secretName: envoy-gateway
EOF
为 Envoy 代理创建一个证书,该证书将存储在 envoy Secret 中。
cat<<EOF | kubectl apply -f -
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
labels:
app.kubernetes.io/name: envoy-gateway
name: envoy
namespace: envoy-gateway-system
spec:
commonName: "*"
dnsNames:
- "*.envoy-gateway-system"
issuerRef:
kind: Issuer
name: eg-issuer
usages:
- "digital signature"
- "data encipherment"
- "key encipherment"
- "content commitment"
secretName: envoy
EOF
创建限流证书,该证书将存储在 envoy-rate-limit Secret 中。
cat<<EOF | kubectl apply -f -
apiVersion: cert-manager.io/v1
kind: Certificate
metadata:
labels:
app.kubernetes.io/name: envoy-gateway
name: envoy-rate-limit
namespace: envoy-gateway-system
spec:
commonName: "*"
dnsNames:
- "*.envoy-gateway-system"
issuerRef:
kind: Issuer
name: eg-issuer
usages:
- "digital signature"
- "data encipherment"
- "key encipherment"
- "content commitment"
secretName: envoy-rate-limit
EOF
现在您可以按照 helm Chart 安装指南使用自定义证书安装 Envoy Gateway。


An Add-ons Helm chart for Envoy Gateway
Homepage: https://gateway.envoyproxy.io/
| Name | Url | |
|---|---|---|
| envoy-gateway-steering-committee | https://github.com/envoyproxy/gateway/blob/main/GOVERNANCE.md | |
| envoy-gateway-maintainers | https://github.com/envoyproxy/gateway/blob/main/CODEOWNERS |
| Repository | Name | Version |
|---|---|---|
| https://fluent.github.io/helm-charts | fluent-bit | 0.30.4 |
| https://grafana.github.io/helm-charts | alloy | 0.9.2 |
| https://grafana.github.io/helm-charts | grafana | 8.0.0 |
| https://grafana.github.io/helm-charts | loki | 4.8.0 |
| https://grafana.github.io/helm-charts | tempo | 1.3.1 |
| https://open-telemetry.github.io/opentelemetry-helm-charts | opentelemetry-collector | 0.108.0 |
| https://prometheus-community.github.io/helm-charts | prometheus | 25.21.0 |
| Key | Type | Default | Description |
|---|---|---|---|
| alloy.alloy.configMap.content | string | "// Write your Alloy config here:\nlogging {\n level = \"info\"\n format = \"logfmt\"\n}\nloki.write \"alloy\" {\n endpoint {\n url = \"http://loki.monitoring.svc:3100/loki/api/v1/push\"\n }\n}\n// discovery.kubernetes allows you to find scrape targets from Kubernetes resources.\n// It watches cluster state and ensures targets are continually synced with what is currently running in your cluster.\ndiscovery.kubernetes \"pod\" {\n role = \"pod\"\n}\n\n// discovery.relabel rewrites the label set of the input targets by applying one or more relabeling rules.\n// If no rules are defined, then the input targets are exported as-is.\ndiscovery.relabel \"pod_logs\" {\n targets = discovery.kubernetes.pod.targets\n\n // Label creation - \"namespace\" field from \"__meta_kubernetes_namespace\"\n rule {\n source_labels = [\"__meta_kubernetes_namespace\"]\n action = \"replace\"\n target_label = \"namespace\"\n }\n\n // Label creation - \"pod\" field from \"__meta_kubernetes_pod_name\"\n rule {\n source_labels = [\"__meta_kubernetes_pod_name\"]\n action = \"replace\"\n target_label = \"pod\"\n }\n\n // Label creation - \"container\" field from \"__meta_kubernetes_pod_container_name\"\n rule {\n source_labels = [\"__meta_kubernetes_pod_container_name\"]\n action = \"replace\"\n target_label = \"container\"\n }\n\n // Label creation - \"app\" field from \"__meta_kubernetes_pod_label_app_kubernetes_io_name\"\n rule {\n source_labels = [\"__meta_kubernetes_pod_label_app_kubernetes_io_name\"]\n action = \"replace\"\n target_label = \"app\"\n }\n\n // Label creation - \"job\" field from \"__meta_kubernetes_namespace\" and \"__meta_kubernetes_pod_container_name\"\n // Concatenate values __meta_kubernetes_namespace/__meta_kubernetes_pod_container_name\n rule {\n source_labels = [\"__meta_kubernetes_namespace\", \"__meta_kubernetes_pod_container_name\"]\n action = \"replace\"\n target_label = \"job\"\n separator = \"/\"\n replacement = \"$1\"\n }\n\n // Label creation - \"container\" field from \"__meta_kubernetes_pod_uid\" and \"__meta_kubernetes_pod_container_name\"\n // Concatenate values __meta_kubernetes_pod_uid/__meta_kubernetes_pod_container_name.log\n rule {\n source_labels = [\"__meta_kubernetes_pod_uid\", \"__meta_kubernetes_pod_container_name\"]\n action = \"replace\"\n target_label = \"__path__\"\n separator = \"/\"\n replacement = \"/var/log/pods/*$1/*.log\"\n }\n\n // Label creation - \"container_runtime\" field from \"__meta_kubernetes_pod_container_id\"\n rule {\n source_labels = [\"__meta_kubernetes_pod_container_id\"]\n action = \"replace\"\n target_label = \"container_runtime\"\n regex = \"^(\\\\S+):\\\\/\\\\/.+$\"\n replacement = \"$1\"\n }\n}\n\n// loki.source.kubernetes tails logs from Kubernetes containers using the Kubernetes API.\nloki.source.kubernetes \"pod_logs\" {\n targets = discovery.relabel.pod_logs.output\n forward_to = [loki.process.pod_logs.receiver]\n}\n// loki.process receives log entries from other Loki components, applies one or more processing stages,\n// and forwards the results to the list of receivers in the component’s arguments.\nloki.process \"pod_logs\" {\n stage.static_labels {\n values = {\n cluster = \"envoy-gateway\",\n }\n }\n\n forward_to = [loki.write.alloy.receiver]\n}" | |
| alloy.enabled | bool | false | |
| alloy.fullnameOverride | string | "alloy" | |
| fluent-bit.config.filters | string | "[FILTER]\n Name kubernetes\n Match kube.*\n Merge_Log On\n Keep_Log Off\n K8S-Logging.Parser On\n K8S-Logging.Exclude On\n\n[FILTER]\n Name grep\n Match kube.*\n Regex $kubernetes['container_name'] ^envoy$\n\n[FILTER]\n Name parser\n Match kube.*\n Key_Name log\n Parser envoy\n Reserve_Data True\n" | |
| fluent-bit.config.inputs | string | "[INPUT]\n Name tail\n Path /var/log/containers/*.log\n multiline.parser docker, cri\n Tag kube.*\n Mem_Buf_Limit 5MB\n Skip_Long_Lines On\n" | |
| fluent-bit.config.outputs | string | "[OUTPUT]\n Name loki\n Match kube.*\n Host loki.monitoring.svc.cluster.local\n Port 3100\n Labels job=fluentbit, app=$kubernetes['labels']['app'], k8s_namespace_name=$kubernetes['namespace_name'], k8s_pod_name=$kubernetes['pod_name'], k8s_container_name=$kubernetes['container_name']\n" | |
| fluent-bit.config.service | string | "[SERVICE]\n Daemon Off\n Flush {{ .Values.flush }}\n Log_Level {{ .Values.logLevel }}\n Parsers_File parsers.conf\n Parsers_File custom_parsers.conf\n HTTP_Server On\n HTTP_Listen 0.0.0.0\n HTTP_Port {{ .Values.metricsPort }}\n Health_Check On\n" | |
| fluent-bit.enabled | bool | true | |
| fluent-bit.fullnameOverride | string | "fluent-bit" | |
| fluent-bit.image.repository | string | "fluent/fluent-bit" | |
| fluent-bit.podAnnotations.“fluentbit.io/exclude” | string | "true" | |
| fluent-bit.podAnnotations.“prometheus.io/path” | string | "/api/v1/metrics/prometheus" | |
| fluent-bit.podAnnotations.“prometheus.io/port” | string | "2020" | |
| fluent-bit.podAnnotations.“prometheus.io/scrape” | string | "true" | |
| fluent-bit.testFramework.enabled | bool | false | |
| grafana.adminPassword | string | "admin" | |
| grafana.dashboardProviders.“dashboardproviders.yaml”.apiVersion | int | 1 | |
| grafana.dashboardProviders.“dashboardproviders.yaml”.providers[0].disableDeletion | bool | false | |
| grafana.dashboardProviders.“dashboardproviders.yaml”.providers[0].editable | bool | true | |
| grafana.dashboardProviders.“dashboardproviders.yaml”.providers[0].folder | string | "envoy-gateway" | |
| grafana.dashboardProviders.“dashboardproviders.yaml”.providers[0].name | string | "envoy-gateway" | |
| grafana.dashboardProviders.“dashboardproviders.yaml”.providers[0].options.path | string | "/var/lib/grafana/dashboards/envoy-gateway" | |
| grafana.dashboardProviders.“dashboardproviders.yaml”.providers[0].orgId | int | 1 | |
| grafana.dashboardProviders.“dashboardproviders.yaml”.providers[0].type | string | "file" | |
| grafana.dashboardsConfigMaps.envoy-gateway | string | "grafana-dashboards" | |
| grafana.datasources.“datasources.yaml”.apiVersion | int | 1 | |
| grafana.datasources.“datasources.yaml”.datasources[0].name | string | "Prometheus" | |
| grafana.datasources.“datasources.yaml”.datasources[0].type | string | "prometheus" | |
| grafana.datasources.“datasources.yaml”.datasources[0].url | string | "http://prometheus" | |
| grafana.enabled | bool | true | |
| grafana.fullnameOverride | string | "grafana" | |
| grafana.service.type | string | "LoadBalancer" | |
| grafana.testFramework.enabled | bool | false | |
| loki.backend.replicas | int | 0 | |
| loki.deploymentMode | string | "SingleBinary" | |
| loki.enabled | bool | true | |
| loki.fullnameOverride | string | "loki" | |
| loki.gateway.enabled | bool | false | |
| loki.loki.auth_enabled | bool | false | |
| loki.loki.commonConfig.replication_factor | int | 1 | |
| loki.loki.compactorAddress | string | "loki" | |
| loki.loki.memberlist | string | "loki-memberlist" | |
| loki.loki.rulerConfig.storage.type | string | "local" | |
| loki.loki.storage.type | string | "filesystem" | |
| loki.monitoring.lokiCanary.enabled | bool | false | |
| loki.monitoring.selfMonitoring.enabled | bool | false | |
| loki.monitoring.selfMonitoring.grafanaAgent.installOperator | bool | false | |
| loki.read.replicas | int | 0 | |
| loki.singleBinary.replicas | int | 1 | |
| loki.test.enabled | bool | false | |
| loki.write.replicas | int | 0 | |
| opentelemetry-collector.config.exporters.debug.verbosity | string | "detailed" | |
| opentelemetry-collector.config.exporters.loki.endpoint | string | "http://loki.monitoring.svc:3100/loki/api/v1/push" | |
| opentelemetry-collector.config.exporters.otlp.endpoint | string | "tempo.monitoring.svc:4317" | |
| opentelemetry-collector.config.exporters.otlp.tls.insecure | bool | true | |
| opentelemetry-collector.config.exporters.prometheus.endpoint | string | "[${env:MY_POD_IP}]:19001" | |
| opentelemetry-collector.config.extensions.health_check.endpoint | string | "[${env:MY_POD_IP}]:13133" | |
| opentelemetry-collector.config.processors.attributes.actions[0].action | string | "insert" | |
| opentelemetry-collector.config.processors.attributes.actions[0].key | string | "loki.attribute.labels" | |
| opentelemetry-collector.config.processors.attributes.actions[0].value | string | "k8s.pod.name, k8s.namespace.name" | |
| opentelemetry-collector.config.receivers.datadog.endpoint | string | "[${env:MY_POD_IP}]:8126" | |
| opentelemetry-collector.config.receivers.jaeger.protocols.grpc.endpoint | string | "[${env:MY_POD_IP}]:14250" | |
| opentelemetry-collector.config.receivers.jaeger.protocols.thrift_compact.endpoint | string | "[${env:MY_POD_IP}]:6831" | |
| opentelemetry-collector.config.receivers.jaeger.protocols.thrift_http.endpoint | string | "[${env:MY_POD_IP}]:14268" | |
| opentelemetry-collector.config.receivers.otlp.protocols.grpc.endpoint | string | "[${env:MY_POD_IP}]:4317" | |
| opentelemetry-collector.config.receivers.otlp.protocols.http.endpoint | string | "[${env:MY_POD_IP}]:4318" | |
| opentelemetry-collector.config.receivers.prometheus.config.scrape_configs[0].job_name | string | "opentelemetry-collector" | |
| opentelemetry-collector.config.receivers.prometheus.config.scrape_configs[0].scrape_interval | string | "10s" | |
| opentelemetry-collector.config.receivers.prometheus.config.scrape_configs[0].static_configs[0].targets[0] | string | "[${env:MY_POD_IP}]:8888" | |
| opentelemetry-collector.config.receivers.zipkin.endpoint | string | "[${env:MY_POD_IP}]:9411" | |
| opentelemetry-collector.config.service.extensions[0] | string | "health_check" | |
| opentelemetry-collector.config.service.pipelines.logs.exporters[0] | string | "loki" | |
| opentelemetry-collector.config.service.pipelines.logs.processors[0] | string | "attributes" | |
| opentelemetry-collector.config.service.pipelines.logs.receivers[0] | string | "otlp" | |
| opentelemetry-collector.config.service.pipelines.metrics.exporters[0] | string | "prometheus" | |
| opentelemetry-collector.config.service.pipelines.metrics.receivers[0] | string | "datadog" | |
| opentelemetry-collector.config.service.pipelines.metrics.receivers[1] | string | "otlp" | |
| opentelemetry-collector.config.service.pipelines.traces.exporters[0] | string | "otlp" | |
| opentelemetry-collector.config.service.pipelines.traces.receivers[0] | string | "datadog" | |
| opentelemetry-collector.config.service.pipelines.traces.receivers[1] | string | "otlp" | |
| opentelemetry-collector.config.service.pipelines.traces.receivers[2] | string | "zipkin" | |
| opentelemetry-collector.config.service.telemetry.metrics.address | string | "[${env:MY_POD_IP}]:8888" | |
| opentelemetry-collector.enabled | bool | false | |
| opentelemetry-collector.fullnameOverride | string | "otel-collector" | |
| opentelemetry-collector.image.repository | string | "otel/opentelemetry-collector-contrib" | |
| opentelemetry-collector.mode | string | "deployment" | |
| prometheus.alertmanager.enabled | bool | false | |
| prometheus.enabled | bool | true | |
| prometheus.kube-state-metrics.enabled | bool | false | |
| prometheus.prometheus-node-exporter.enabled | bool | false | |
| prometheus.prometheus-pushgateway.enabled | bool | false | |
| prometheus.server.fullnameOverride | string | "prometheus" | |
| prometheus.server.global.scrape_interval | string | "15s" | |
| prometheus.server.image.repository | string | "prom/prometheus" | |
| prometheus.server.persistentVolume.enabled | bool | false | |
| prometheus.server.readinessProbeInitialDelay | int | 0 | |
| prometheus.server.securityContext | object | {} | |
| prometheus.server.service.type | string | "LoadBalancer" | |
| tempo.enabled | bool | true | |
| tempo.fullnameOverride | string | "tempo" | |
| tempo.service.type | string | "LoadBalancer" |


The Helm chart for Envoy Gateway
Homepage: https://gateway.envoyproxy.io/
| Name | Url | |
|---|---|---|
| envoy-gateway-steering-committee | https://github.com/envoyproxy/gateway/blob/main/GOVERNANCE.md | |
| envoy-gateway-maintainers | https://github.com/envoyproxy/gateway/blob/main/CODEOWNERS |
| Key | Type | Default | Description |
|---|---|---|---|
| certgen | object | {"job":{"affinity":{},"annotations":{},"args":[],"nodeSelector":{},"resources":{},"securityContext":{"allowPrivilegeEscalation":false,"capabilities":{"drop":["ALL"]},"privileged":false,"readOnlyRootFilesystem":true,"runAsGroup":65534,"runAsNonRoot":true,"runAsUser":65534,"seccompProfile":{"type":"RuntimeDefault"}},"tolerations":[],"ttlSecondsAfterFinished":30},"rbac":{"annotations":{},"labels":{}}} | Certgen is used to generate the certificates required by EnvoyGateway. If you want to construct a custom certificate, you can generate a custom certificate through Cert-Manager before installing EnvoyGateway. Certgen will not overwrite the custom certificate. Please do not manually modify values.yaml to disable certgen, it may cause EnvoyGateway OIDC,OAuth2,etc. to not work as expected. |
| config.envoyGateway.gateway.controllerName | string | "gateway.envoyproxy.io/gatewayclass-controller" | |
| config.envoyGateway.logging.level.default | string | "info" | |
| config.envoyGateway.provider.type | string | "Kubernetes" | |
| createNamespace | bool | false | |
| deployment.envoyGateway.image.repository | string | "" | |
| deployment.envoyGateway.image.tag | string | "" | |
| deployment.envoyGateway.imagePullPolicy | string | "" | |
| deployment.envoyGateway.imagePullSecrets | list | [] | |
| deployment.envoyGateway.resources.limits.memory | string | "1024Mi" | |
| deployment.envoyGateway.resources.requests.cpu | string | "100m" | |
| deployment.envoyGateway.resources.requests.memory | string | "256Mi" | |
| deployment.envoyGateway.securityContext.allowPrivilegeEscalation | bool | false | |
| deployment.envoyGateway.securityContext.capabilities.drop[0] | string | "ALL" | |
| deployment.envoyGateway.securityContext.privileged | bool | false | |
| deployment.envoyGateway.securityContext.runAsGroup | int | 65532 | |
| deployment.envoyGateway.securityContext.runAsNonRoot | bool | true | |
| deployment.envoyGateway.securityContext.runAsUser | int | 65532 | |
| deployment.envoyGateway.securityContext.seccompProfile.type | string | "RuntimeDefault" | |
| deployment.pod.affinity | object | {} | |
| deployment.pod.annotations.“prometheus.io/port” | string | "19001" | |
| deployment.pod.annotations.“prometheus.io/scrape” | string | "true" | |
| deployment.pod.labels | object | {} | |
| deployment.pod.nodeSelector | object | {} | |
| deployment.pod.tolerations | list | [] | |
| deployment.pod.topologySpreadConstraints | list | [] | |
| deployment.ports[0].name | string | "grpc" | |
| deployment.ports[0].port | int | 18000 | |
| deployment.ports[0].targetPort | int | 18000 | |
| deployment.ports[1].name | string | "ratelimit" | |
| deployment.ports[1].port | int | 18001 | |
| deployment.ports[1].targetPort | int | 18001 | |
| deployment.ports[2].name | string | "wasm" | |
| deployment.ports[2].port | int | 18002 | |
| deployment.ports[2].targetPort | int | 18002 | |
| deployment.ports[3].name | string | "metrics" | |
| deployment.ports[3].port | int | 19001 | |
| deployment.ports[3].targetPort | int | 19001 | |
| deployment.priorityClassName | string | nil | |
| deployment.replicas | int | 1 | |
| global.images.envoyGateway.image | string | nil | |
| global.images.envoyGateway.pullPolicy | string | nil | |
| global.images.envoyGateway.pullSecrets | list | [] | |
| global.images.ratelimit.image | string | "docker.io/envoyproxy/ratelimit:master" | |
| global.images.ratelimit.pullPolicy | string | "IfNotPresent" | |
| global.images.ratelimit.pullSecrets | list | [] | |
| kubernetesClusterDomain | string | "cluster.local" | |
| podDisruptionBudget.minAvailable | int | 0 | |
| service.annotations | object | {} |
Envoy Gateway 依赖于 Envoy Proxy 和 Gateway API,并在 Kubernetes 集群中运行。 这些产品的所有版本并非都可以与 Envoy Gateway 一起运行。下面列出了支持的版本组合; 粗体类型表示实际编译到每个 Envoy Gateway 版本中的 Envoy Proxy 和 Gateway API 的版本。
| Envoy Gateway 版本 | Envoy Proxy 版本 | Rate Limit 版本 | Gateway API 版本 | Kubernetes 版本 |
|---|---|---|---|---|
| v1.0.0 | distroless-v1.29.2 | 19f2079f | v1.0.0 | v1.26, v1.27, v1.28, v1.29 |
| v0.6.0 | distroless-v1.28-latest | b9796237 | v1.0.0 | v1.26, v1.27, v1.28 |
| v0.5.0 | v1.27-latest | e059638d | v0.7.1 | v1.25, v1.26, v1.27 |
| v0.4.0 | v1.26-latest | 542a6047 | v0.6.2 | v1.25, v1.26, v1.27 |
| v0.3.0 | v1.25-latest | f28024e3 | v0.6.1 | v1.24, v1.25, v1.26 |
| v0.2.0 | v1.23-latest | v0.5.1 | v1.24 | |
| latest | dev-latest | master | v1.0.0 | v1.29, v1.30, v1.31, v1.32 |
Package v1alpha1 contains API schema definitions for the gateway.envoyproxy.io API group.
Underlying type: string
ALPNProtocol specifies the protocol to be negotiated using ALPN
Appears in:
| Value | Description |
|---|---|
http/1.0 | HTTPProtocolVersion1_0 specifies that HTTP/1.0 should be negotiable with ALPN |
http/1.1 | HTTPProtocolVersion1_1 specifies that HTTP/1.1 should be negotiable with ALPN |
h2 | HTTPProtocolVersion2 specifies that HTTP/2 should be negotiable with ALPN |
ALSEnvoyProxyAccessLog defines the gRPC Access Log Service (ALS) sink. The service must implement the Envoy gRPC Access Log Service streaming API: https://www.envoyproxy.io/docs/envoy/latest/api-v3/service/accesslog/v3/als.proto Access log format information is passed in the form of gRPC metadata when the stream is established.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. | |
logName | string | false | LogName defines the friendly name of the access log to be returned in StreamAccessLogsMessage.Identifier. This allows the access log server to differentiate between different access logs coming from the same Envoy. | |
type | ALSEnvoyProxyAccessLogType | true | Type defines the type of accesslog. Supported types are “HTTP” and “TCP”. | |
http | ALSEnvoyProxyHTTPAccessLogConfig | false | HTTP defines additional configuration specific to HTTP access logs. |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
HTTP | ALSEnvoyProxyAccessLogTypeHTTP defines the HTTP access log type and will populate StreamAccessLogsMessage.http_logs. |
TCP | ALSEnvoyProxyAccessLogTypeTCP defines the TCP access log type and will populate StreamAccessLogsMessage.tcp_logs. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
requestHeaders | string array | false | RequestHeaders defines request headers to include in log entries sent to the access log service. | |
responseHeaders | string array | false | ResponseHeaders defines response headers to include in log entries sent to the access log service. | |
responseTrailers | string array | false | ResponseTrailers defines response trailers to include in log entries sent to the access log service. |
APIKeyAuth defines the configuration for the API Key Authentication.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
credentialRefs | SecretObjectReference array | true | CredentialRefs is the Kubernetes secret which contains the API keys. This is an Opaque secret. Each API key is stored in the key representing the client id. If the secrets have a key for a duplicated client, the first one will be used. | |
extractFrom | ExtractFrom array | true | ExtractFrom is where to fetch the key from the coming request. The value from the first source that has a key will be used. |
ActiveHealthCheck defines the active health check configuration. EG supports various types of active health checking including HTTP, TCP.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
timeout | Duration | false | 1s | Timeout defines the time to wait for a health check response. |
interval | Duration | false | 3s | Interval defines the time between active health checks. |
unhealthyThreshold | integer | false | 3 | UnhealthyThreshold defines the number of unhealthy health checks required before a backend host is marked unhealthy. |
healthyThreshold | integer | false | 1 | HealthyThreshold defines the number of healthy health checks required before a backend host is marked healthy. |
type | ActiveHealthCheckerType | true | Type defines the type of health checker. | |
http | HTTPActiveHealthChecker | false | HTTP defines the configuration of http health checker. It’s required while the health checker type is HTTP. | |
tcp | TCPActiveHealthChecker | false | TCP defines the configuration of tcp health checker. It’s required while the health checker type is TCP. | |
grpc | GRPCActiveHealthChecker | false | GRPC defines the configuration of the GRPC health checker. It’s optional, and can only be used if the specified type is GRPC. |
ActiveHealthCheckPayload defines the encoding of the payload bytes in the payload.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | ActiveHealthCheckPayloadType | true | Type defines the type of the payload. | |
text | string | false | Text payload in plain text. | |
binary | integer array | false | Binary payload base64 encoded. |
Underlying type: string
ActiveHealthCheckPayloadType is the type of the payload.
Appears in:
| Value | Description |
|---|---|
Text | ActiveHealthCheckPayloadTypeText defines the Text type payload. |
Binary | ActiveHealthCheckPayloadTypeBinary defines the Binary type payload. |
Underlying type: string
ActiveHealthCheckerType is the type of health checker.
Appears in:
| Value | Description |
|---|---|
HTTP | ActiveHealthCheckerTypeHTTP defines the HTTP type of health checking. |
TCP | ActiveHealthCheckerTypeTCP defines the TCP type of health checking. |
GRPC | ActiveHealthCheckerTypeGRPC defines the GRPC type of health checking. |
Underlying type: string
AppProtocolType defines various backend applications protocols supported by Envoy Gateway
Appears in:
| Value | Description |
|---|---|
gateway.envoyproxy.io/h2c | AppProtocolTypeH2C defines the HTTP/2 application protocol. |
gateway.envoyproxy.io/ws | AppProtocolTypeWS defines the WebSocket over HTTP protocol. |
gateway.envoyproxy.io/wss | AppProtocolTypeWSS defines the WebSocket over HTTPS protocol. |
Authorization defines the authorization configuration.
Note: if neither Rules nor DefaultAction is specified, the default action is to deny all requests.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
rules | AuthorizationRule array | false | Rules defines a list of authorization rules. These rules are evaluated in order, the first matching rule will be applied, and the rest will be skipped. For example, if there are two rules: the first rule allows the request and the second rule denies it, when a request matches both rules, it will be allowed. | |
defaultAction | AuthorizationAction | false | DefaultAction defines the default action to be taken if no rules match. If not specified, the default action is Deny. |
Underlying type: string
AuthorizationAction defines the action to be taken if a rule matches.
Appears in:
| Value | Description |
|---|---|
Allow | AuthorizationActionAllow is the action to allow the request. |
Deny | AuthorizationActionDeny is the action to deny the request. |
AuthorizationRule defines a single authorization rule.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | false | Name is a user-friendly name for the rule. If not specified, Envoy Gateway will generate a unique name for the rule. | |
action | AuthorizationAction | true | Action defines the action to be taken if the rule matches. | |
principal | Principal | true | Principal specifies the client identity of a request. If there are multiple principal types, all principals must match for the rule to match. For example, if there are two principals: one for client IP and one for JWT claim, the rule will match only if both the client IP and the JWT claim match. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
baseInterval | Duration | true | BaseInterval is the base interval between retries. | |
maxInterval | Duration | false | MaxInterval is the maximum interval between retries. This parameter is optional, but must be greater than or equal to the base_interval if set. The default is 10 times the base_interval |
Backend allows the user to configure the endpoints of a backend and the behavior of the connection from Envoy Proxy to the backend.
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | Backend | ||
metadata | ObjectMeta | true | Refer to Kubernetes API documentation for fields of metadata. | |
spec | BackendSpec | true | Spec defines the desired state of Backend. | |
status | BackendStatus | true | Status defines the current status of Backend. |
BackendCluster contains all the configuration required for configuring access to a backend. This can include multiple endpoints, and settings that apply for managing the connection to all these endpoints.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. |
BackendConnection allows users to configure connection-level settings of backend
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
bufferLimit | Quantity | false | BufferLimit Soft limit on size of the cluster’s connections read and write buffers. BufferLimit applies to connection streaming (maybe non-streaming) channel between processes, it’s in user space. If unspecified, an implementation defined default is applied (32768 bytes). For example, 20Mi, 1Gi, 256Ki etc. Note: that when the suffix is not provided, the value is interpreted as bytes. |
BackendEndpoint describes a backend endpoint, which can be either a fully-qualified domain name, IP address or unix domain socket corresponding to Envoy’s Address: https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/core/v3/address.proto#config-core-v3-address
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
fqdn | FQDNEndpoint | false | FQDN defines a FQDN endpoint | |
ip | IPEndpoint | false | IP defines an IP endpoint. Supports both IPv4 and IPv6 addresses. | |
unix | UnixSocket | false | Unix defines the unix domain socket endpoint |
BackendRef defines how an ObjectReference that is specific to BackendRef.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
group | Group | false | Group is the group of the referent. For example, “gateway.networking.k8s.io”. When unspecified or empty string, core API group is inferred. | |
kind | Kind | false | Service | Kind is the Kubernetes resource kind of the referent. For example “Service”. Defaults to “Service” when not specified. ExternalName services can refer to CNAME DNS records that may live outside of the cluster and as such are difficult to reason about in terms of conformance. They also may not be safe to forward to (see CVE-2021-25740 for more information). Implementations SHOULD NOT support ExternalName Services. Support: Core (Services with a type other than ExternalName) Support: Implementation-specific (Services with type ExternalName) |
name | ObjectName | true | Name is the name of the referent. | |
namespace | Namespace | false | Namespace is the namespace of the backend. When unspecified, the local namespace is inferred. Note that when a namespace different than the local namespace is specified, a ReferenceGrant object is required in the referent namespace to allow that namespace’s owner to accept the reference. See the ReferenceGrant documentation for details. Support: Core | |
port | PortNumber | false | Port specifies the destination port number to use for this resource. Port is required when the referent is a Kubernetes Service. In this case, the port number is the service port number, not the target port. For other resources, destination port might be derived from the referent resource or this field. | |
fallback | boolean | false | Fallback indicates whether the backend is designated as a fallback. Multiple fallback backends can be configured. It is highly recommended to configure active or passive health checks to ensure that failover can be detected when the active backends become unhealthy and to automatically readjust once the primary backends are healthy again. The overprovisioning factor is set to 1.4, meaning the fallback backends will only start receiving traffic when the health of the active backends falls below 72%. |
BackendSpec describes the desired state of BackendSpec.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
endpoints | BackendEndpoint array | true | Endpoints defines the endpoints to be used when connecting to the backend. | |
appProtocols | AppProtocolType array | false | AppProtocols defines the application protocols to be supported when connecting to the backend. | |
fallback | boolean | false | Fallback indicates whether the backend is designated as a fallback. It is highly recommended to configure active or passive health checks to ensure that failover can be detected when the active backends become unhealthy and to automatically readjust once the primary backends are healthy again. The overprovisioning factor is set to 1.4, meaning the fallback backends will only start receiving traffic when the health of the active backends falls below 72%. |
BackendStatus defines the state of Backend
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
conditions | Condition array | false | Conditions describe the current conditions of the Backend. |
BackendTLSConfig describes the BackendTLS configuration for Envoy Proxy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
clientCertificateRef | SecretObjectReference | false | ClientCertificateRef defines the reference to a Kubernetes Secret that contains the client certificate and private key for Envoy to use when connecting to backend services and external services, such as ExtAuth, ALS, OpenTelemetry, etc. This secret should be located within the same namespace as the Envoy proxy resource that references it. | |
minVersion | TLSVersion | false | Min specifies the minimal TLS protocol version to allow. The default is TLS 1.2 if this is not specified. | |
maxVersion | TLSVersion | false | Max specifies the maximal TLS protocol version to allow The default is TLS 1.3 if this is not specified. | |
ciphers | string array | false | Ciphers specifies the set of cipher suites supported when negotiating TLS 1.0 - 1.2. This setting has no effect for TLS 1.3. In non-FIPS Envoy Proxy builds the default cipher list is: - [ECDHE-ECDSA-AES128-GCM-SHA256|ECDHE-ECDSA-CHACHA20-POLY1305] - [ECDHE-RSA-AES128-GCM-SHA256|ECDHE-RSA-CHACHA20-POLY1305] - ECDHE-ECDSA-AES256-GCM-SHA384 - ECDHE-RSA-AES256-GCM-SHA384 In builds using BoringSSL FIPS the default cipher list is: - ECDHE-ECDSA-AES128-GCM-SHA256 - ECDHE-RSA-AES128-GCM-SHA256 - ECDHE-ECDSA-AES256-GCM-SHA384 - ECDHE-RSA-AES256-GCM-SHA384 | |
ecdhCurves | string array | false | ECDHCurves specifies the set of supported ECDH curves. In non-FIPS Envoy Proxy builds the default curves are: - X25519 - P-256 In builds using BoringSSL FIPS the default curve is: - P-256 | |
signatureAlgorithms | string array | false | SignatureAlgorithms specifies which signature algorithms the listener should support. | |
alpnProtocols | ALPNProtocol array | false | ALPNProtocols supplies the list of ALPN protocols that should be exposed by the listener or used by the proxy to connect to the backend. Defaults: 1. HTTPS Routes: h2 and http/1.1 are enabled in listener context. 2. Other Routes: ALPN is disabled. 3. Backends: proxy uses the appropriate ALPN options for the backend protocol. When an empty list is provided, the ALPN TLS extension is disabled. Supported values are: - http/1.0 - http/1.1 - h2 |
BackendTrafficPolicy allows the user to configure the behavior of the connection between the Envoy Proxy listener and the backend service.
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | BackendTrafficPolicy | ||
metadata | ObjectMeta | true | Refer to Kubernetes API documentation for fields of metadata. | |
spec | BackendTrafficPolicySpec | true | spec defines the desired state of BackendTrafficPolicy. | |
status | PolicyStatus | true | status defines the current status of BackendTrafficPolicy. |
BackendTrafficPolicySpec defines the desired state of BackendTrafficPolicy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
targetRef | LocalPolicyTargetReferenceWithSectionName | true | TargetRef is the name of the resource this policy is being attached to. This policy and the TargetRef MUST be in the same namespace for this Policy to have effect Deprecated: use targetRefs/targetSelectors instead | |
targetRefs | LocalPolicyTargetReferenceWithSectionName array | true | TargetRefs are the names of the Gateway resources this policy is being attached to. | |
targetSelectors | TargetSelector array | true | TargetSelectors allow targeting resources for this policy based on labels | |
loadBalancer | LoadBalancer | false | LoadBalancer policy to apply when routing traffic from the gateway to the backend endpoints. Defaults to LeastRequest. | |
retry | Retry | false | Retry provides more advanced usage, allowing users to customize the number of retries, retry fallback strategy, and retry triggering conditions. If not set, retry will be disabled. | |
proxyProtocol | ProxyProtocol | false | ProxyProtocol enables the Proxy Protocol when communicating with the backend. | |
tcpKeepalive | TCPKeepalive | false | TcpKeepalive settings associated with the upstream client connection. Disabled by default. | |
healthCheck | HealthCheck | false | HealthCheck allows gateway to perform active health checking on backends. | |
circuitBreaker | CircuitBreaker | false | Circuit Breaker settings for the upstream connections and requests. If not set, circuit breakers will be enabled with the default thresholds | |
timeout | Timeout | false | Timeout settings for the backend connections. | |
connection | BackendConnection | false | Connection includes backend connection settings. | |
dns | DNS | false | DNS includes dns resolution settings. | |
http2 | HTTP2Settings | false | HTTP2 provides HTTP/2 configuration for backend connections. | |
rateLimit | RateLimitSpec | false | RateLimit allows the user to limit the number of incoming requests to a predefined value based on attributes within the traffic flow. | |
faultInjection | FaultInjection | false | FaultInjection defines the fault injection policy to be applied. This configuration can be used to inject delays and abort requests to mimic failure scenarios such as service failures and overloads | |
useClientProtocol | boolean | false | UseClientProtocol configures Envoy to prefer sending requests to backends using the same HTTP protocol that the incoming request used. Defaults to false, which means that Envoy will use the protocol indicated by the attached BackendRef. | |
compression | Compression array | false | The compression config for the http streams. | |
responseOverride | ResponseOverride array | false | ResponseOverride defines the configuration to override specific responses with a custom one. If multiple configurations are specified, the first one to match wins. |
BasicAuth defines the configuration for the HTTP Basic Authentication.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
users | SecretObjectReference | true | The Kubernetes secret which contains the username-password pairs in htpasswd format, used to verify user credentials in the “Authorization” header. This is an Opaque secret. The username-password pairs should be stored in the key “.htpasswd”. As the key name indicates, the value needs to be the htpasswd format, for example: “user1:{SHA}hashed_user1_password”. Right now, only SHA hash algorithm is supported. Reference to https://httpd.apache.org/docs/2.4/programs/htpasswd.html for more details. Note: The secret must be in the same namespace as the SecurityPolicy. |
BodyToExtAuth defines the Body to Ext Auth configuration
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
maxRequestBytes | integer | true | MaxRequestBytes is the maximum size of a message body that the filter will hold in memory. Envoy will return HTTP 413 and will not initiate the authorization process when buffer reaches the number set in this field. Note that this setting will have precedence over failOpen mode. |
Underlying type: string
BootstrapType defines the types of bootstrap supported by Envoy Gateway.
Appears in:
| Value | Description |
|---|---|
Merge | Merge merges the provided bootstrap with the default one. The provided bootstrap can add or override a value within a map, or add a new value to a list. Please note that the provided bootstrap can’t override a value within a list. |
Replace | Replace replaces the default bootstrap with the provided one. |
JSONPatch | JSONPatch applies the provided JSONPatches to the default bootstrap. |
BrotliCompressor defines the config for the Brotli compressor. The default values can be found here: https://www.envoyproxy.io/docs/envoy/latest/api-v3/extensions/compression/brotli/compressor/v3/brotli.proto#extension-envoy-compression-brotli-compressor
Appears in:
Underlying type: string
CIDR defines a CIDR Address range. A CIDR can be an IPv4 address range such as “192.168.1.0/24” or an IPv6 address range such as “2001:0db8:11a3:09d7::/64”.
Appears in:
CORS defines the configuration for Cross-Origin Resource Sharing (CORS).
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
allowOrigins | Origin array | false | AllowOrigins defines the origins that are allowed to make requests. It specifies the allowed origins in the Access-Control-Allow-Origin CORS response header. The value “*” allows any origin to make requests. | |
allowMethods | string array | false | AllowMethods defines the methods that are allowed to make requests. It specifies the allowed methods in the Access-Control-Allow-Methods CORS response header.. The value “*” allows any method to be used. | |
allowHeaders | string array | false | AllowHeaders defines the headers that are allowed to be sent with requests. It specifies the allowed headers in the Access-Control-Allow-Headers CORS response header.. The value “*” allows any header to be sent. | |
exposeHeaders | string array | false | ExposeHeaders defines which response headers should be made accessible to scripts running in the browser. It specifies the headers in the Access-Control-Expose-Headers CORS response header.. The value “*” allows any header to be exposed. | |
maxAge | Duration | false | MaxAge defines how long the results of a preflight request can be cached. It specifies the value in the Access-Control-Max-Age CORS response header.. | |
allowCredentials | boolean | false | AllowCredentials indicates whether a request can include user credentials like cookies, authentication headers, or TLS client certificates. It specifies the value in the Access-Control-Allow-Credentials CORS response header. |
CircuitBreaker defines the Circuit Breaker configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
maxConnections | integer | false | 1024 | The maximum number of connections that Envoy will establish to the referenced backend defined within a xRoute rule. |
maxPendingRequests | integer | false | 1024 | The maximum number of pending requests that Envoy will queue to the referenced backend defined within a xRoute rule. |
maxParallelRequests | integer | false | 1024 | The maximum number of parallel requests that Envoy will make to the referenced backend defined within a xRoute rule. |
maxParallelRetries | integer | false | 1024 | The maximum number of parallel retries that Envoy will make to the referenced backend defined within a xRoute rule. |
maxRequestsPerConnection | integer | false | The maximum number of requests that Envoy will make over a single connection to the referenced backend defined within a xRoute rule. Default: unlimited. |
ClaimToHeader defines a configuration to convert JWT claims into HTTP headers
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
header | string | true | Header defines the name of the HTTP request header that the JWT Claim will be saved into. | |
claim | string | true | Claim is the JWT Claim that should be saved into the header : it can be a nested claim of type (eg. “claim.nested.key”, “sub”). The nested claim name must use dot “." to separate the JSON name path. |
ClientConnection allows users to configure connection-level settings of client
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
connectionLimit | ConnectionLimit | false | ConnectionLimit defines limits related to connections | |
bufferLimit | Quantity | false | BufferLimit provides configuration for the maximum buffer size in bytes for each incoming connection. BufferLimit applies to connection streaming (maybe non-streaming) channel between processes, it’s in user space. For example, 20Mi, 1Gi, 256Ki etc. Note that when the suffix is not provided, the value is interpreted as bytes. Default: 32768 bytes. |
ClientIPDetectionSettings provides configuration for determining the original client IP address for requests.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
xForwardedFor | XForwardedForSettings | false | XForwardedForSettings provides configuration for using X-Forwarded-For headers for determining the client IP address. | |
customHeader | CustomHeaderExtensionSettings | false | CustomHeader provides configuration for determining the client IP address for a request based on a trusted custom HTTP header. This uses the custom_header original IP detection extension. Refer to https://www.envoyproxy.io/docs/envoy/latest/api-v3/extensions/http/original_ip_detection/custom_header/v3/custom_header.proto for more details. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
clientValidation | ClientValidationContext | false | ClientValidation specifies the configuration to validate the client initiating the TLS connection to the Gateway listener. | |
minVersion | TLSVersion | false | Min specifies the minimal TLS protocol version to allow. The default is TLS 1.2 if this is not specified. | |
maxVersion | TLSVersion | false | Max specifies the maximal TLS protocol version to allow The default is TLS 1.3 if this is not specified. | |
ciphers | string array | false | Ciphers specifies the set of cipher suites supported when negotiating TLS 1.0 - 1.2. This setting has no effect for TLS 1.3. In non-FIPS Envoy Proxy builds the default cipher list is: - [ECDHE-ECDSA-AES128-GCM-SHA256|ECDHE-ECDSA-CHACHA20-POLY1305] - [ECDHE-RSA-AES128-GCM-SHA256|ECDHE-RSA-CHACHA20-POLY1305] - ECDHE-ECDSA-AES256-GCM-SHA384 - ECDHE-RSA-AES256-GCM-SHA384 In builds using BoringSSL FIPS the default cipher list is: - ECDHE-ECDSA-AES128-GCM-SHA256 - ECDHE-RSA-AES128-GCM-SHA256 - ECDHE-ECDSA-AES256-GCM-SHA384 - ECDHE-RSA-AES256-GCM-SHA384 | |
ecdhCurves | string array | false | ECDHCurves specifies the set of supported ECDH curves. In non-FIPS Envoy Proxy builds the default curves are: - X25519 - P-256 In builds using BoringSSL FIPS the default curve is: - P-256 | |
signatureAlgorithms | string array | false | SignatureAlgorithms specifies which signature algorithms the listener should support. | |
alpnProtocols | ALPNProtocol array | false | ALPNProtocols supplies the list of ALPN protocols that should be exposed by the listener or used by the proxy to connect to the backend. Defaults: 1. HTTPS Routes: h2 and http/1.1 are enabled in listener context. 2. Other Routes: ALPN is disabled. 3. Backends: proxy uses the appropriate ALPN options for the backend protocol. When an empty list is provided, the ALPN TLS extension is disabled. Supported values are: - http/1.0 - http/1.1 - h2 | |
session | Session | false | Session defines settings related to TLS session management. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
tcp | TCPClientTimeout | false | Timeout settings for TCP. | |
http | HTTPClientTimeout | false | Timeout settings for HTTP. |
ClientTrafficPolicy allows the user to configure the behavior of the connection between the downstream client and Envoy Proxy listener.
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | ClientTrafficPolicy | ||
metadata | ObjectMeta | true | Refer to Kubernetes API documentation for fields of metadata. | |
spec | ClientTrafficPolicySpec | true | Spec defines the desired state of ClientTrafficPolicy. | |
status | PolicyStatus | true | Status defines the current status of ClientTrafficPolicy. |
ClientTrafficPolicySpec defines the desired state of ClientTrafficPolicy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
targetRef | LocalPolicyTargetReferenceWithSectionName | true | TargetRef is the name of the resource this policy is being attached to. This policy and the TargetRef MUST be in the same namespace for this Policy to have effect Deprecated: use targetRefs/targetSelectors instead | |
targetRefs | LocalPolicyTargetReferenceWithSectionName array | true | TargetRefs are the names of the Gateway resources this policy is being attached to. | |
targetSelectors | TargetSelector array | true | TargetSelectors allow targeting resources for this policy based on labels | |
tcpKeepalive | TCPKeepalive | false | TcpKeepalive settings associated with the downstream client connection. If defined, sets SO_KEEPALIVE on the listener socket to enable TCP Keepalives. Disabled by default. | |
enableProxyProtocol | boolean | false | EnableProxyProtocol interprets the ProxyProtocol header and adds the Client Address into the X-Forwarded-For header. Note Proxy Protocol must be present when this field is set, else the connection is closed. | |
clientIPDetection | ClientIPDetectionSettings | false | ClientIPDetectionSettings provides configuration for determining the original client IP address for requests. | |
tls | ClientTLSSettings | false | TLS settings configure TLS termination settings with the downstream client. | |
path | PathSettings | false | Path enables managing how the incoming path set by clients can be normalized. | |
headers | HeaderSettings | false | HeaderSettings provides configuration for header management. | |
timeout | ClientTimeout | false | Timeout settings for the client connections. | |
connection | ClientConnection | false | Connection includes client connection settings. | |
http1 | HTTP1Settings | false | HTTP1 provides HTTP/1 configuration on the listener. | |
http2 | HTTP2Settings | false | HTTP2 provides HTTP/2 configuration on the listener. | |
http3 | HTTP3Settings | false | HTTP3 provides HTTP/3 configuration on the listener. | |
healthCheck | HealthCheckSettings | false | HealthCheck provides configuration for determining whether the HTTP/HTTPS listener is healthy. |
ClientValidationContext holds configuration that can be used to validate the client initiating the TLS connection to the Gateway. By default, no client specific configuration is validated.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
optional | boolean | false | Optional set to true accepts connections even when a client doesn’t present a certificate. Defaults to false, which rejects connections without a valid client certificate. | |
caCertificateRefs | SecretObjectReference array | false | CACertificateRefs contains one or more references to Kubernetes objects that contain TLS certificates of the Certificate Authorities that can be used as a trust anchor to validate the certificates presented by the client. A single reference to a Kubernetes ConfigMap or a Kubernetes Secret, with the CA certificate in a key named ca.crt is currently supported.References to a resource in different namespace are invalid UNLESS there is a ReferenceGrant in the target namespace that allows the certificate to be attached. |
ClusterSettings provides the various knobs that can be set to control how traffic to a given backend will be configured.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
loadBalancer | LoadBalancer | false | LoadBalancer policy to apply when routing traffic from the gateway to the backend endpoints. Defaults to LeastRequest. | |
retry | Retry | false | Retry provides more advanced usage, allowing users to customize the number of retries, retry fallback strategy, and retry triggering conditions. If not set, retry will be disabled. | |
proxyProtocol | ProxyProtocol | false | ProxyProtocol enables the Proxy Protocol when communicating with the backend. | |
tcpKeepalive | TCPKeepalive | false | TcpKeepalive settings associated with the upstream client connection. Disabled by default. | |
healthCheck | HealthCheck | false | HealthCheck allows gateway to perform active health checking on backends. | |
circuitBreaker | CircuitBreaker | false | Circuit Breaker settings for the upstream connections and requests. If not set, circuit breakers will be enabled with the default thresholds | |
timeout | Timeout | false | Timeout settings for the backend connections. | |
connection | BackendConnection | false | Connection includes backend connection settings. | |
dns | DNS | false | DNS includes dns resolution settings. | |
http2 | HTTP2Settings | false | HTTP2 provides HTTP/2 configuration for backend connections. |
Compression defines the config of enabling compression. This can help reduce the bandwidth at the expense of higher CPU.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | CompressorType | true | CompressorType defines the compressor type to use for compression. | |
brotli | BrotliCompressor | false | The configuration for Brotli compressor. | |
gzip | GzipCompressor | false | The configuration for GZIP compressor. |
Underlying type: string
CompressorType defines the types of compressor library supported by Envoy Gateway.
Appears in:
| Value | Description |
|---|---|
Gzip | |
Brotli |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
value | integer | true | Value of the maximum concurrent connections limit. When the limit is reached, incoming connections will be closed after the CloseDelay duration. | |
closeDelay | Duration | false | CloseDelay defines the delay to use before closing connections that are rejected once the limit value is reached. Default: none. |
ConsistentHash defines the configuration related to the consistent hash load balancer policy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | ConsistentHashType | true | ConsistentHashType defines the type of input to hash on. Valid Type values are “SourceIP”, “Header”, “Cookie”. | |
header | Header | false | Header configures the header hash policy when the consistent hash type is set to Header. | |
cookie | Cookie | false | Cookie configures the cookie hash policy when the consistent hash type is set to Cookie. | |
tableSize | integer | false | 65537 | The table size for consistent hashing, must be prime number limited to 5000011. |
Underlying type: string
ConsistentHashType defines the type of input to hash on.
Appears in:
| Value | Description |
|---|---|
SourceIP | SourceIPConsistentHashType hashes based on the source IP address. |
Header | HeaderConsistentHashType hashes based on a request header. |
Cookie | CookieConsistentHashType hashes based on a cookie. |
Cookie defines the cookie hashing configuration for consistent hash based load balancing.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | true | Name of the cookie to hash. If this cookie does not exist in the request, Envoy will generate a cookie and set the TTL on the response back to the client based on Layer 4 attributes of the backend endpoint, to ensure that these future requests go to the same backend endpoint. Make sure to set the TTL field for this case. | |
ttl | Duration | false | TTL of the generated cookie if the cookie is not present. This value sets the Max-Age attribute value. | |
attributes | object (keys:string, values:string) | false | Additional Attributes to set for the generated cookie. |
CustomHeaderExtensionSettings provides configuration for determining the client IP address for a request based on a trusted custom HTTP header. This uses the the custom_header original IP detection extension. Refer to https://www.envoyproxy.io/docs/envoy/latest/api-v3/extensions/http/original_ip_detection/custom_header/v3/custom_header.proto for more details.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | true | Name of the header containing the original downstream remote address, if present. | |
failClosed | boolean | false | FailClosed is a switch used to control the flow of traffic when client IP detection fails. If set to true, the listener will respond with 403 Forbidden when the client IP address cannot be determined. |
CustomResponse defines the configuration for returning a custom response.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
contentType | string | false | Content Type of the response. This will be set in the Content-Type header. | |
body | CustomResponseBody | true | Body of the Custom Response |
CustomResponseBody
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | ResponseValueType | true | Inline | Type is the type of method to use to read the body value. Valid values are Inline and ValueRef, default is Inline. |
inline | string | false | Inline contains the value as an inline string. | |
valueRef | LocalObjectReference | false | ValueRef contains the contents of the body specified as a local object reference. Only a reference to ConfigMap is supported. The value of key response.body in the ConfigMap will be used as the response body.If the key is not found, the first value in the ConfigMap will be used. |
CustomResponseMatch defines the configuration for matching a user response to return a custom one.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
statusCodes | StatusCodeMatch array | true | Status code to match on. The match evaluates to true if any of the matches are successful. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | CustomTagType | true | Literal | Type defines the type of custom tag. |
literal | LiteralCustomTag | true | Literal adds hard-coded value to each span. It’s required when the type is “Literal”. | |
environment | EnvironmentCustomTag | true | Environment adds value from environment variable to each span. It’s required when the type is “Environment”. | |
requestHeader | RequestHeaderCustomTag | true | RequestHeader adds value from request header to each span. It’s required when the type is “RequestHeader”. |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
Literal | CustomTagTypeLiteral adds hard-coded value to each span. |
Environment | CustomTagTypeEnvironment adds value from environment variable to each span. |
RequestHeader | CustomTagTypeRequestHeader adds value from request header to each span. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
dnsRefreshRate | Duration | true | DNSRefreshRate specifies the rate at which DNS records should be refreshed. Defaults to 30 seconds. | |
respectDnsTtl | boolean | true | RespectDNSTTL indicates whether the DNS Time-To-Live (TTL) should be respected. If the value is set to true, the DNS refresh rate will be set to the resource record’s TTL. Defaults to true. |
EnvironmentCustomTag adds value from environment variable to each span.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | true | Name defines the name of the environment variable which to extract the value from. | |
defaultValue | string | false | DefaultValue defines the default value to use if the environment variable is not set. |
EnvoyExtensionPolicy allows the user to configure various envoy extensibility options for the Gateway.
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | EnvoyExtensionPolicy | ||
metadata | ObjectMeta | true | Refer to Kubernetes API documentation for fields of metadata. | |
spec | EnvoyExtensionPolicySpec | true | Spec defines the desired state of EnvoyExtensionPolicy. | |
status | PolicyStatus | true | Status defines the current status of EnvoyExtensionPolicy. |
EnvoyExtensionPolicySpec defines the desired state of EnvoyExtensionPolicy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
targetRef | LocalPolicyTargetReferenceWithSectionName | true | TargetRef is the name of the resource this policy is being attached to. This policy and the TargetRef MUST be in the same namespace for this Policy to have effect Deprecated: use targetRefs/targetSelectors instead | |
targetRefs | LocalPolicyTargetReferenceWithSectionName array | true | TargetRefs are the names of the Gateway resources this policy is being attached to. | |
targetSelectors | TargetSelector array | true | TargetSelectors allow targeting resources for this policy based on labels | |
wasm | Wasm array | false | Wasm is a list of Wasm extensions to be loaded by the Gateway. Order matters, as the extensions will be loaded in the order they are defined in this list. | |
extProc | ExtProc array | false | ExtProc is an ordered list of external processing filters that should be added to the envoy filter chain |
Underlying type: string
EnvoyFilter defines the type of Envoy HTTP filter.
Appears in:
| Value | Description |
|---|---|
envoy.filters.http.health_check | EnvoyFilterHealthCheck defines the Envoy HTTP health check filter. |
envoy.filters.http.fault | EnvoyFilterFault defines the Envoy HTTP fault filter. |
envoy.filters.http.cors | EnvoyFilterCORS defines the Envoy HTTP CORS filter. |
envoy.filters.http.ext_authz | EnvoyFilterExtAuthz defines the Envoy HTTP external authorization filter. |
envoy.filters.http.api_key_auth | EnvoyFilterAPIKeyAuth defines the Envoy HTTP api key authentication filter. |
envoy.filters.http.basic_auth | EnvoyFilterBasicAuth defines the Envoy HTTP basic authentication filter. |
envoy.filters.http.oauth2 | EnvoyFilterOAuth2 defines the Envoy HTTP OAuth2 filter. |
envoy.filters.http.jwt_authn | EnvoyFilterJWTAuthn defines the Envoy HTTP JWT authentication filter. |
envoy.filters.http.stateful_session | EnvoyFilterSessionPersistence defines the Envoy HTTP session persistence filter. |
envoy.filters.http.ext_proc | EnvoyFilterExtProc defines the Envoy HTTP external process filter. |
envoy.filters.http.wasm | EnvoyFilterWasm defines the Envoy HTTP WebAssembly filter. |
envoy.filters.http.rbac | EnvoyFilterRBAC defines the Envoy RBAC filter. |
envoy.filters.http.local_ratelimit | EnvoyFilterLocalRateLimit defines the Envoy HTTP local rate limit filter. |
envoy.filters.http.ratelimit | EnvoyFilterRateLimit defines the Envoy HTTP rate limit filter. |
envoy.filters.http.custom_response | EnvoyFilterCustomResponse defines the Envoy HTTP custom response filter. |
envoy.filters.http.compressor | EnvoyFilterCompressor defines the Envoy HTTP compressor filter. |
envoy.filters.http.router | EnvoyFilterRouter defines the Envoy HTTP router filter. |
EnvoyGateway is the schema for the envoygateways API.
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | EnvoyGateway | ||
gateway | Gateway | false | Gateway defines desired Gateway API specific configuration. If unset, default configuration parameters will apply. | |
provider | EnvoyGatewayProvider | false | Provider defines the desired provider and provider-specific configuration. If unspecified, the Kubernetes provider is used with default configuration parameters. | |
logging | EnvoyGatewayLogging | false | { default:info } | Logging defines logging parameters for Envoy Gateway. |
admin | EnvoyGatewayAdmin | false | Admin defines the desired admin related abilities. If unspecified, the Admin is used with default configuration parameters. | |
telemetry | EnvoyGatewayTelemetry | false | Telemetry defines the desired control plane telemetry related abilities. If unspecified, the telemetry is used with default configuration. | |
rateLimit | RateLimit | false | RateLimit defines the configuration associated with the Rate Limit service deployed by Envoy Gateway required to implement the Global Rate limiting functionality. The specific rate limit service used here is the reference implementation in Envoy. For more details visit https://github.com/envoyproxy/ratelimit. This configuration is unneeded for “Local” rate limiting. | |
extensionManager | ExtensionManager | false | ExtensionManager defines an extension manager to register for the Envoy Gateway Control Plane. | |
extensionApis | ExtensionAPISettings | false | ExtensionAPIs defines the settings related to specific Gateway API Extensions implemented by Envoy Gateway |
EnvoyGatewayAdmin defines the Envoy Gateway Admin configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
address | EnvoyGatewayAdminAddress | false | Address defines the address of Envoy Gateway Admin Server. | |
enableDumpConfig | boolean | false | EnableDumpConfig defines if enable dump config in Envoy Gateway logs. | |
enablePprof | boolean | false | EnablePprof defines if enable pprof in Envoy Gateway Admin Server. |
EnvoyGatewayAdminAddress defines the Envoy Gateway Admin Address configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
port | integer | false | 19000 | Port defines the port the admin server is exposed on. |
host | string | false | 127.0.0.1 | Host defines the admin server hostname. |
EnvoyGatewayCustomProvider defines configuration for the Custom provider.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
resource | EnvoyGatewayResourceProvider | true | Resource defines the desired resource provider. This provider is used to specify the provider to be used to retrieve the resource configurations such as Gateway API resources | |
infrastructure | EnvoyGatewayInfrastructureProvider | false | Infrastructure defines the desired infrastructure provider. This provider is used to specify the provider to be used to provide an environment to deploy the out resources like the Envoy Proxy data plane. Infrastructure is optional, if provider is not specified, No infrastructure provider is available. |
EnvoyGatewayFileResourceProvider defines configuration for the File Resource provider.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
paths | string array | true | Paths are the paths to a directory or file containing the resource configuration. Recursive subdirectories are not currently supported. |
EnvoyGatewayHostInfrastructureProvider defines configuration for the Host Infrastructure provider.
Appears in:
EnvoyGatewayInfrastructureProvider defines configuration for the Custom Infrastructure provider.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | InfrastructureProviderType | true | Type is the type of infrastructure providers to use. Supported types are “Host”. | |
host | EnvoyGatewayHostInfrastructureProvider | false | Host defines the configuration of the Host provider. Host provides runtime deployment of the data plane as a child process on the host environment. |
EnvoyGatewayKubernetesProvider defines configuration for the Kubernetes provider.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
rateLimitDeployment | KubernetesDeploymentSpec | false | RateLimitDeployment defines the desired state of the Envoy ratelimit deployment resource. If unspecified, default settings for the managed Envoy ratelimit deployment resource are applied. | |
rateLimitHpa | KubernetesHorizontalPodAutoscalerSpec | false | RateLimitHpa defines the Horizontal Pod Autoscaler settings for Envoy ratelimit Deployment. If the HPA is set, Replicas field from RateLimitDeployment will be ignored. | |
watch | KubernetesWatchMode | false | Watch holds configuration of which input resources should be watched and reconciled. | |
deploy | KubernetesDeployMode | false | Deploy holds configuration of how output managed resources such as the Envoy Proxy data plane should be deployed | |
overwriteControlPlaneCerts | boolean | false | OverwriteControlPlaneCerts updates the secrets containing the control plane certs, when set. | |
leaderElection | LeaderElection | false | LeaderElection specifies the configuration for leader election. If it’s not set up, leader election will be active by default, using Kubernetes’ standard settings. | |
shutdownManager | ShutdownManager | false | ShutdownManager defines the configuration for the shutdown manager. |
Underlying type: string
EnvoyGatewayLogComponent defines a component that supports a configured logging level.
Appears in:
| Value | Description |
|---|---|
default | LogComponentGatewayDefault defines the “default”-wide logging component. When specified, all other logging components are ignored. |
provider | LogComponentProviderRunner defines the “provider” runner component. |
gateway-api | LogComponentGatewayAPIRunner defines the “gateway-api” runner component. |
xds-translator | LogComponentXdsTranslatorRunner defines the “xds-translator” runner component. |
xds-server | LogComponentXdsServerRunner defines the “xds-server” runner component. |
infrastructure | LogComponentInfrastructureRunner defines the “infrastructure” runner component. |
global-ratelimit | LogComponentGlobalRateLimitRunner defines the “global-ratelimit” runner component. |
EnvoyGatewayLogging defines logging for Envoy Gateway.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
level | object (keys:EnvoyGatewayLogComponent, values:LogLevel) | true | { default:info } | Level is the logging level. If unspecified, defaults to “info”. EnvoyGatewayLogComponent options: default/provider/gateway-api/xds-translator/xds-server/infrastructure/global-ratelimit. LogLevel options: debug/info/error/warn. |
EnvoyGatewayMetricSink defines control plane metric sinks where metrics are sent to.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | MetricSinkType | true | OpenTelemetry | Type defines the metric sink type. EG control plane currently supports OpenTelemetry. |
openTelemetry | EnvoyGatewayOpenTelemetrySink | true | OpenTelemetry defines the configuration for OpenTelemetry sink. It’s required if the sink type is OpenTelemetry. |
EnvoyGatewayMetrics defines control plane push/pull metrics configurations.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
sinks | EnvoyGatewayMetricSink array | true | Sinks defines the metric sinks where metrics are sent to. | |
prometheus | EnvoyGatewayPrometheusProvider | true | Prometheus defines the configuration for prometheus endpoint. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
host | string | true | Host define the sink service hostname. | |
protocol | string | true | Protocol define the sink service protocol. | |
port | integer | false | 4317 | Port defines the port the sink service is exposed on. |
exportInterval | Duration | true | ExportInterval configures the intervening time between exports for a Sink. This option overrides any value set for the OTEL_METRIC_EXPORT_INTERVAL environment variable. If ExportInterval is less than or equal to zero, 60 seconds is used as the default. | |
exportTimeout | Duration | true | ExportTimeout configures the time a Sink waits for an export to complete before canceling it. This option overrides any value set for the OTEL_METRIC_EXPORT_TIMEOUT environment variable. If ExportTimeout is less than or equal to zero, 30 seconds is used as the default. |
EnvoyGatewayPrometheusProvider will expose prometheus endpoint in pull mode.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
disable | boolean | true | Disable defines if disables the prometheus metrics in pull mode. |
EnvoyGatewayProvider defines the desired configuration of a provider.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | ProviderType | true | Type is the type of provider to use. Supported types are “Kubernetes”, “Custom”. | |
kubernetes | EnvoyGatewayKubernetesProvider | false | Kubernetes defines the configuration of the Kubernetes provider. Kubernetes provides runtime configuration via the Kubernetes API. | |
custom | EnvoyGatewayCustomProvider | false | Custom defines the configuration for the Custom provider. This provider allows you to define a specific resource provider and an infrastructure provider. |
EnvoyGatewayResourceProvider defines configuration for the Custom Resource provider.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | ResourceProviderType | true | Type is the type of resource provider to use. Supported types are “File”. | |
file | EnvoyGatewayFileResourceProvider | false | File defines the configuration of the File provider. File provides runtime configuration defined by one or more files. |
EnvoyGatewaySpec defines the desired state of Envoy Gateway.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
gateway | Gateway | false | Gateway defines desired Gateway API specific configuration. If unset, default configuration parameters will apply. | |
provider | EnvoyGatewayProvider | false | Provider defines the desired provider and provider-specific configuration. If unspecified, the Kubernetes provider is used with default configuration parameters. | |
logging | EnvoyGatewayLogging | false | { default:info } | Logging defines logging parameters for Envoy Gateway. |
admin | EnvoyGatewayAdmin | false | Admin defines the desired admin related abilities. If unspecified, the Admin is used with default configuration parameters. | |
telemetry | EnvoyGatewayTelemetry | false | Telemetry defines the desired control plane telemetry related abilities. If unspecified, the telemetry is used with default configuration. | |
rateLimit | RateLimit | false | RateLimit defines the configuration associated with the Rate Limit service deployed by Envoy Gateway required to implement the Global Rate limiting functionality. The specific rate limit service used here is the reference implementation in Envoy. For more details visit https://github.com/envoyproxy/ratelimit. This configuration is unneeded for “Local” rate limiting. | |
extensionManager | ExtensionManager | false | ExtensionManager defines an extension manager to register for the Envoy Gateway Control Plane. | |
extensionApis | ExtensionAPISettings | false | ExtensionAPIs defines the settings related to specific Gateway API Extensions implemented by Envoy Gateway |
EnvoyGatewayTelemetry defines telemetry configurations for envoy gateway control plane. Control plane will focus on metrics observability telemetry and tracing telemetry later.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
metrics | EnvoyGatewayMetrics | true | Metrics defines metrics configuration for envoy gateway. |
EnvoyJSONPatchConfig defines the configuration for patching a Envoy xDS Resource using JSONPatch semantic
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | EnvoyResourceType | true | Type is the typed URL of the Envoy xDS Resource | |
name | string | true | Name is the name of the resource | |
operation | JSONPatchOperation | true | Patch defines the JSON Patch Operation |
EnvoyPatchPolicy allows the user to modify the generated Envoy xDS resources by Envoy Gateway using this patch API
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | EnvoyPatchPolicy | ||
metadata | ObjectMeta | true | Refer to Kubernetes API documentation for fields of metadata. | |
spec | EnvoyPatchPolicySpec | true | Spec defines the desired state of EnvoyPatchPolicy. | |
status | PolicyStatus | true | Status defines the current status of EnvoyPatchPolicy. |
EnvoyPatchPolicySpec defines the desired state of EnvoyPatchPolicy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | EnvoyPatchType | true | Type decides the type of patch. Valid EnvoyPatchType values are “JSONPatch”. | |
jsonPatches | EnvoyJSONPatchConfig array | false | JSONPatch defines the JSONPatch configuration. | |
targetRef | LocalPolicyTargetReference | true | TargetRef is the name of the Gateway API resource this policy is being attached to. By default, attaching to Gateway is supported and when mergeGateways is enabled it should attach to GatewayClass. This Policy and the TargetRef MUST be in the same namespace for this Policy to have effect and be applied to the Gateway TargetRef | |
priority | integer | true | Priority of the EnvoyPatchPolicy. If multiple EnvoyPatchPolicies are applied to the same TargetRef, they will be applied in the ascending order of the priority i.e. int32.min has the highest priority and int32.max has the lowest priority. Defaults to 0. |
Underlying type: string
EnvoyPatchType specifies the types of Envoy patching mechanisms.
Appears in:
| Value | Description |
|---|---|
JSONPatch | JSONPatchEnvoyPatchType allows the user to patch the generated xDS resources using JSONPatch semantics. For more details on the semantics, please refer to https://datatracker.ietf.org/doc/html/rfc6902 |
EnvoyProxy is the schema for the envoyproxies API.
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | EnvoyProxy | ||
metadata | ObjectMeta | true | Refer to Kubernetes API documentation for fields of metadata. | |
spec | EnvoyProxySpec | true | EnvoyProxySpec defines the desired state of EnvoyProxy. | |
status | EnvoyProxyStatus | true | EnvoyProxyStatus defines the actual state of EnvoyProxy. |
EnvoyProxyKubernetesProvider defines configuration for the Kubernetes resource provider.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
envoyDeployment | KubernetesDeploymentSpec | false | EnvoyDeployment defines the desired state of the Envoy deployment resource. If unspecified, default settings for the managed Envoy deployment resource are applied. | |
envoyDaemonSet | KubernetesDaemonSetSpec | false | EnvoyDaemonSet defines the desired state of the Envoy daemonset resource. Disabled by default, a deployment resource is used instead to provision the Envoy Proxy fleet | |
envoyService | KubernetesServiceSpec | false | EnvoyService defines the desired state of the Envoy service resource. If unspecified, default settings for the managed Envoy service resource are applied. | |
envoyHpa | KubernetesHorizontalPodAutoscalerSpec | false | EnvoyHpa defines the Horizontal Pod Autoscaler settings for Envoy Proxy Deployment. Once the HPA is being set, Replicas field from EnvoyDeployment will be ignored. | |
useListenerPortAsContainerPort | boolean | false | UseListenerPortAsContainerPort disables the port shifting feature in the Envoy Proxy. When set to false (default value), if the service port is a privileged port (1-1023), add a constant to the value converting it into an ephemeral port. This allows the container to bind to the port without needing a CAP_NET_BIND_SERVICE capability. | |
envoyPDB | KubernetesPodDisruptionBudgetSpec | false | EnvoyPDB allows to control the pod disruption budget of an Envoy Proxy. |
EnvoyProxyProvider defines the desired state of a resource provider.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | ProviderType | true | Type is the type of resource provider to use. A resource provider provides infrastructure resources for running the data plane, e.g. Envoy proxy, and optional auxiliary control planes. Supported types are “Kubernetes”. | |
kubernetes | EnvoyProxyKubernetesProvider | false | Kubernetes defines the desired state of the Kubernetes resource provider. Kubernetes provides infrastructure resources for running the data plane, e.g. Envoy proxy. If unspecified and type is “Kubernetes”, default settings for managed Kubernetes resources are applied. |
EnvoyProxySpec defines the desired state of EnvoyProxy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
provider | EnvoyProxyProvider | false | Provider defines the desired resource provider and provider-specific configuration. If unspecified, the “Kubernetes” resource provider is used with default configuration parameters. | |
logging | ProxyLogging | true | { level:map[default:warn] } | Logging defines logging parameters for managed proxies. |
telemetry | ProxyTelemetry | false | Telemetry defines telemetry parameters for managed proxies. | |
bootstrap | ProxyBootstrap | false | Bootstrap defines the Envoy Bootstrap as a YAML string. Visit https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/bootstrap/v3/bootstrap.proto#envoy-v3-api-msg-config-bootstrap-v3-bootstrap to learn more about the syntax. If set, this is the Bootstrap configuration used for the managed Envoy Proxy fleet instead of the default Bootstrap configuration set by Envoy Gateway. Some fields within the Bootstrap that are required to communicate with the xDS Server (Envoy Gateway) and receive xDS resources from it are not configurable and will result in the EnvoyProxy resource being rejected.Backward compatibility across minor versions is not guaranteed. We strongly recommend using egctl x translate to generate a EnvoyProxy resource with the Bootstrap field set to the defaultBootstrap configuration used. You can edit this configuration, and rerun egctl x translate to ensure there are no validation errors. | |
concurrency | integer | false | Concurrency defines the number of worker threads to run. If unset, it defaults to the number of cpuset threads on the platform. | |
routingType | RoutingType | false | RoutingType can be set to “Service” to use the Service Cluster IP for routing to the backend, or it can be set to “Endpoint” to use Endpoint routing. The default is “Endpoint”. | |
extraArgs | string array | false | ExtraArgs defines additional command line options that are provided to Envoy. More info: https://www.envoyproxy.io/docs/envoy/latest/operations/cli#command-line-options Note: some command line options are used internally(e.g. –log-level) so they cannot be provided here. | |
mergeGateways | boolean | false | MergeGateways defines if Gateway resources should be merged onto the same Envoy Proxy Infrastructure. Setting this field to true would merge all Gateway Listeners under the parent Gateway Class. This means that the port, protocol and hostname tuple must be unique for every listener. If a duplicate listener is detected, the newer listener (based on timestamp) will be rejected and its status will be updated with a “Accepted=False” condition. | |
shutdown | ShutdownConfig | false | Shutdown defines configuration for graceful envoy shutdown process. | |
filterOrder | FilterPosition array | false | FilterOrder defines the order of filters in the Envoy proxy’s HTTP filter chain. The FilterPosition in the list will be applied in the order they are defined. If unspecified, the default filter order is applied. Default filter order is: - envoy.filters.http.health_check - envoy.filters.http.fault - envoy.filters.http.cors - envoy.filters.http.ext_authz - envoy.filters.http.basic_auth - envoy.filters.http.oauth2 - envoy.filters.http.jwt_authn - envoy.filters.http.stateful_session - envoy.filters.http.ext_proc - envoy.filters.http.wasm - envoy.filters.http.rbac - envoy.filters.http.local_ratelimit - envoy.filters.http.ratelimit - envoy.filters.http.custom_response - envoy.filters.http.router Note: “envoy.filters.http.router” cannot be reordered, it’s always the last filter in the chain. | |
backendTLS | BackendTLSConfig | false | BackendTLS is the TLS configuration for the Envoy proxy to use when connecting to backends. These settings are applied on backends for which TLS policies are specified. | |
ipFamily | IPFamily | false | IPFamily specifies the IP family for the EnvoyProxy fleet. This setting only affects the Gateway listener port and does not impact other aspects of the Envoy proxy configuration. If not specified, the system will operate as follows: - It defaults to IPv4 only. - IPv6 and dual-stack environments are not supported in this default configuration. Note: To enable IPv6 or dual-stack functionality, explicit configuration is required. | |
preserveRouteOrder | boolean | false | PreserveRouteOrder determines if the order of matching for HTTPRoutes is determined by Gateway-API specification (https://gateway-api.sigs.k8s.io/reference/spec/#gateway.networking.k8s.io/v1.HTTPRouteRule) or preserves the order defined by users in the HTTPRoute’s HTTPRouteRule list. Default: False |
EnvoyProxyStatus defines the observed state of EnvoyProxy. This type is not implemented until https://github.com/envoyproxy/gateway/issues/1007 is fixed.
Appears in:
Underlying type: string
EnvoyResourceType specifies the type URL of the Envoy resource.
Appears in:
| Value | Description |
|---|---|
type.googleapis.com/envoy.config.listener.v3.Listener | ListenerEnvoyResourceType defines the Type URL of the Listener resource |
type.googleapis.com/envoy.config.route.v3.RouteConfiguration | RouteConfigurationEnvoyResourceType defines the Type URL of the RouteConfiguration resource |
type.googleapis.com/envoy.config.cluster.v3.Cluster | ClusterEnvoyResourceType defines the Type URL of the Cluster resource |
type.googleapis.com/envoy.config.endpoint.v3.ClusterLoadAssignment | ClusterLoadAssignmentEnvoyResourceType defines the Type URL of the ClusterLoadAssignment resource |
ExtAuth defines the configuration for External Authorization.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
grpc | GRPCExtAuthService | true | GRPC defines the gRPC External Authorization service. Either GRPCService or HTTPService must be specified, and only one of them can be provided. | |
http | HTTPExtAuthService | true | HTTP defines the HTTP External Authorization service. Either GRPCService or HTTPService must be specified, and only one of them can be provided. | |
headersToExtAuth | string array | false | HeadersToExtAuth defines the client request headers that will be included in the request to the external authorization service. Note: If not specified, the default behavior for gRPC and HTTP external authorization services is different due to backward compatibility reasons. All headers will be included in the check request to a gRPC authorization server. Only the following headers will be included in the check request to an HTTP authorization server: Host, Method, Path, Content-Length, and Authorization. And these headers will always be included to the check request to an HTTP authorization server by default, no matter whether they are specified in HeadersToExtAuth or not. | |
bodyToExtAuth | BodyToExtAuth | false | BodyToExtAuth defines the Body to Ext Auth configuration. | |
failOpen | boolean | false | false | FailOpen is a switch used to control the behavior when a response from the External Authorization service cannot be obtained. If FailOpen is set to true, the system allows the traffic to pass through. Otherwise, if it is set to false or not set (defaulting to false), the system blocks the traffic and returns a HTTP 5xx error, reflecting a fail-closed approach. This setting determines whether to prioritize accessibility over strict security in case of authorization service failure. |
recomputeRoute | boolean | false | RecomputeRoute clears the route cache and recalculates the routing decision. This field must be enabled if the headers added or modified by the ExtAuth are used for route matching decisions. If the recomputation selects a new route, features targeting the new matched route will be applied. |
ExtProc defines the configuration for External Processing filter.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. | |
messageTimeout | Duration | false | MessageTimeout is the timeout for a response to be returned from the external processor Default: 200ms | |
failOpen | boolean | false | FailOpen defines if requests or responses that cannot be processed due to connectivity to the external processor are terminated or passed-through. Default: false | |
processingMode | ExtProcProcessingMode | false | ProcessingMode defines how request and response body is processed Default: header and body are not sent to the external processor | |
metadata | ExtProcMetadata | false | Refer to Kubernetes API documentation for fields of metadata. |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
Streamed | StreamedExtProcBodyProcessingMode will stream the body to the server in pieces as they arrive at the proxy. |
Buffered | BufferedExtProcBodyProcessingMode will buffer the message body in memory and send the entire body at once. If the body exceeds the configured buffer limit, then the downstream system will receive an error. |
BufferedPartial | BufferedPartialExtBodyHeaderProcessingMode will buffer the message body in memory and send the entire body in one chunk. If the body exceeds the configured buffer limit, then the body contents up to the buffer limit will be sent. |
ExtProcMetadata defines options related to the sending and receiving of dynamic metadata to and from the external processor service
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
accessibleNamespaces | string array | false | AccessibleNamespaces are metadata namespaces that are sent to the external processor as context | |
writableNamespaces | string array | false | WritableNamespaces are metadata namespaces that the external processor can write to |
ExtProcProcessingMode defines if and how headers and bodies are sent to the service. https://www.envoyproxy.io/docs/envoy/latest/api-v3/extensions/filters/http/ext_proc/v3/processing_mode.proto#envoy-v3-api-msg-extensions-filters-http-ext-proc-v3-processingmode
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
request | ProcessingModeOptions | false | Defines processing mode for requests. If present, request headers are sent. Request body is processed according to the specified mode. | |
response | ProcessingModeOptions | false | Defines processing mode for responses. If present, response headers are sent. Response body is processed according to the specified mode. |
ExtensionAPISettings defines the settings specific to Gateway API Extensions.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
enableEnvoyPatchPolicy | boolean | true | EnableEnvoyPatchPolicy enables Envoy Gateway to reconcile and implement the EnvoyPatchPolicy resources. | |
enableBackend | boolean | true | EnableBackend enables Envoy Gateway to reconcile and implement the Backend resources. |
ExtensionHooks defines extension hooks across all supported runners
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
xdsTranslator | XDSTranslatorHooks | true | XDSTranslator defines all the supported extension hooks for the xds-translator runner |
ExtensionManager defines the configuration for registering an extension manager to the Envoy Gateway control plane.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
resources | GroupVersionKind array | false | Resources defines the set of K8s resources the extension will handle as route filter resources | |
policyResources | GroupVersionKind array | false | PolicyResources defines the set of K8S resources the extension server will handle as directly attached GatewayAPI policies | |
hooks | ExtensionHooks | true | Hooks defines the set of hooks the extension supports | |
service | ExtensionService | true | Service defines the configuration of the extension service that the Envoy Gateway Control Plane will call through extension hooks. | |
failOpen | boolean | false | FailOpen defines if Envoy Gateway should ignore errors returned from the Extension Service hooks. The default is false, which means Envoy Gateway will fail closed if the Extension Service returns an error. Fail-close means that if the Extension Service hooks return an error, the relevant route/listener/resource will be replaced with a default configuration returning Internal Server Error (HTTP 500). Fail-open means that if the Extension Service hooks return an error, no changes will be applied to the source of the configuration which was sent to the extension server. |
ExtensionService defines the configuration for connecting to a registered extension service.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
fqdn | FQDNEndpoint | false | FQDN defines a FQDN endpoint | |
ip | IPEndpoint | false | IP defines an IP endpoint. Supports both IPv4 and IPv6 addresses. | |
unix | UnixSocket | false | Unix defines the unix domain socket endpoint | |
host | string | false | Host define the extension service hostname. Deprecated: use the appropriate transport attribute instead (FQDN,IP,Unix) | |
port | integer | false | 80 | Port defines the port the extension service is exposed on. Deprecated: use the appropriate transport attribute instead (FQDN,IP,Unix) |
tls | ExtensionTLS | false | TLS defines TLS configuration for communication between Envoy Gateway and the extension service. |
ExtensionTLS defines the TLS configuration when connecting to an extension service
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
certificateRef | SecretObjectReference | true | CertificateRef contains a references to objects (Kubernetes objects or otherwise) that contains a TLS certificate and private keys. These certificates are used to establish a TLS handshake to the extension server. CertificateRef can only reference a Kubernetes Secret at this time. |
ExtractFrom is where to fetch the key from the coming request. Only one of header, param or cookie is supposed to be specified.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
headers | string array | false | Headers is the names of the header to fetch the key from. If multiple headers are specified, envoy will look for the api key in the order of the list. This field is optional, but only one of headers, params or cookies is supposed to be specified. | |
params | string array | false | Params is the names of the query parameter to fetch the key from. If multiple params are specified, envoy will look for the api key in the order of the list. This field is optional, but only one of headers, params or cookies is supposed to be specified. | |
cookies | string array | false | Cookies is the names of the cookie to fetch the key from. If multiple cookies are specified, envoy will look for the api key in the order of the list. This field is optional, but only one of headers, params or cookies is supposed to be specified. |
FQDNEndpoint describes TCP/UDP socket address, corresponding to Envoy’s Socket Address https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/core/v3/address.proto#config-core-v3-socketaddress
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
hostname | string | true | Hostname defines the FQDN hostname of the backend endpoint. | |
port | integer | true | Port defines the port of the backend endpoint. |
FaultInjection defines the fault injection policy to be applied. This configuration can be used to inject delays and abort requests to mimic failure scenarios such as service failures and overloads
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
delay | FaultInjectionDelay | false | If specified, a delay will be injected into the request. | |
abort | FaultInjectionAbort | false | If specified, the request will be aborted if it meets the configuration criteria. |
FaultInjectionAbort defines the abort fault injection configuration
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
httpStatus | integer | false | StatusCode specifies the HTTP status code to be returned | |
grpcStatus | integer | false | GrpcStatus specifies the GRPC status code to be returned | |
percentage | float | false | 100 | Percentage specifies the percentage of requests to be aborted. Default 100%, if set 0, no requests will be aborted. Accuracy to 0.0001%. |
FaultInjectionDelay defines the delay fault injection configuration
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
fixedDelay | Duration | true | FixedDelay specifies the fixed delay duration | |
percentage | float | false | 100 | Percentage specifies the percentage of requests to be delayed. Default 100%, if set 0, no requests will be delayed. Accuracy to 0.0001%. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
path | string | true | Path defines the file path used to expose envoy access log(e.g. /dev/stdout). |
FilterPosition defines the position of an Envoy HTTP filter in the filter chain.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | EnvoyFilter | true | Name of the filter. | |
before | EnvoyFilter | true | Before defines the filter that should come before the filter. Only one of Before or After must be set. | |
after | EnvoyFilter | true | After defines the filter that should come after the filter. Only one of Before or After must be set. |
GRPCActiveHealthChecker defines the settings of the GRPC health check.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
service | string | false | Service to send in the health check request. If this is not specified, then the health check request applies to the entire server and not to a specific service. |
GRPCExtAuthService defines the gRPC External Authorization service The authorization request message is defined in https://www.envoyproxy.io/docs/envoy/latest/api-v3/service/auth/v3/external_auth.proto
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. |
Gateway defines the desired Gateway API configuration of Envoy Gateway.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
controllerName | string | false | ControllerName defines the name of the Gateway API controller. If unspecified, defaults to “gateway.envoyproxy.io/gatewayclass-controller”. See the following for additional details: https://gateway-api.sigs.k8s.io/reference/spec/#gateway.networking.k8s.io/v1.GatewayClass |
GlobalRateLimit defines global rate limit configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
rules | RateLimitRule array | true | Rules are a list of RateLimit selectors and limits. Each rule and its associated limit is applied in a mutually exclusive way. If a request matches multiple rules, each of their associated limits get applied, so a single request might increase the rate limit counters for multiple rules if selected. The rate limit service will return a logical OR of the individual rate limit decisions of all matching rules. For example, if a request matches two rules, one rate limited and one not, the final decision will be to rate limit the request. |
GroupVersionKind unambiguously identifies a Kind. It can be converted to k8s.io/apimachinery/pkg/runtime/schema.GroupVersionKind
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
group | string | true | ||
version | string | true | ||
kind | string | true |
GzipCompressor defines the config for the Gzip compressor. The default values can be found here: https://www.envoyproxy.io/docs/envoy/latest/api-v3/extensions/compression/gzip/compressor/v3/gzip.proto#extension-envoy-compression-gzip-compressor
Appears in:
HTTP10Settings provides HTTP/1.0 configuration on the listener.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
useDefaultHost | boolean | false | UseDefaultHost defines if the HTTP/1.0 request is missing the Host header, then the hostname associated with the listener should be injected into the request. If this is not set and an HTTP/1.0 request arrives without a host, then it will be rejected. |
HTTP1Settings provides HTTP/1 configuration on the listener.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
enableTrailers | boolean | false | EnableTrailers defines if HTTP/1 trailers should be proxied by Envoy. | |
preserveHeaderCase | boolean | false | PreserveHeaderCase defines if Envoy should preserve the letter case of headers. By default, Envoy will lowercase all the headers. | |
http10 | HTTP10Settings | false | HTTP10 turns on support for HTTP/1.0 and HTTP/0.9 requests. |
HTTP2Settings provides HTTP/2 configuration for listeners and backends.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
initialStreamWindowSize | Quantity | false | InitialStreamWindowSize sets the initial window size for HTTP/2 streams. If not set, the default value is 64 KiB(64*1024). | |
initialConnectionWindowSize | Quantity | false | InitialConnectionWindowSize sets the initial window size for HTTP/2 connections. If not set, the default value is 1 MiB. | |
maxConcurrentStreams | integer | false | MaxConcurrentStreams sets the maximum number of concurrent streams allowed per connection. If not set, the default value is 100. | |
onInvalidMessage | InvalidMessageAction | false | OnInvalidMessage determines if Envoy will terminate the connection or just the offending stream in the event of HTTP messaging error It’s recommended for L2 Envoy deployments to set this value to TerminateStream. https://www.envoyproxy.io/docs/envoy/latest/configuration/best_practices/level_two Default: TerminateConnection |
HTTP3Settings provides HTTP/3 configuration on the listener.
Appears in:
HTTPActiveHealthChecker defines the settings of http health check.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
path | string | true | Path defines the HTTP path that will be requested during health checking. | |
method | string | false | Method defines the HTTP method used for health checking. Defaults to GET | |
expectedStatuses | HTTPStatus array | false | ExpectedStatuses defines a list of HTTP response statuses considered healthy. Defaults to 200 only | |
expectedResponse | ActiveHealthCheckPayload | false | ExpectedResponse defines a list of HTTP expected responses to match. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
requestReceivedTimeout | Duration | false | RequestReceivedTimeout is the duration envoy waits for the complete request reception. This timer starts upon request initiation and stops when either the last byte of the request is sent upstream or when the response begins. | |
idleTimeout | Duration | false | IdleTimeout for an HTTP connection. Idle time is defined as a period in which there are no active requests in the connection. Default: 1 hour. |
HTTPDirectResponseFilter defines the configuration to return a fixed response.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
contentType | string | false | Content Type of the response. This will be set in the Content-Type header. | |
body | CustomResponseBody | false | Body of the Response | |
statusCode | integer | false | Status Code of the HTTP response If unset, defaults to 200. |
HTTPExtAuthService defines the HTTP External Authorization service
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. | |
path | string | true | Path is the path of the HTTP External Authorization service. If path is specified, the authorization request will be sent to that path, or else the authorization request will be sent to the root path. | |
headersToBackend | string array | false | HeadersToBackend are the authorization response headers that will be added to the original client request before sending it to the backend server. Note that coexisting headers will be overridden. If not specified, no authorization response headers will be added to the original client request. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | HTTPHostnameModifierType | true | ||
header | string | false | Header is the name of the header whose value would be used to rewrite the Host header |
Underlying type: string
HTTPPathModifierType defines the type of Hostname rewrite.
Appears in:
| Value | Description |
|---|---|
Header | HeaderHTTPHostnameModifier indicates that the Host header value would be replaced with the value of the header specified in header. https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#envoy-v3-api-field-config-route-v3-routeaction-host-rewrite-header |
Backend | BackendHTTPHostnameModifier indicates that the Host header value would be replaced by the DNS name of the backend if it exists. https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#envoy-v3-api-field-config-route-v3-routeaction-auto-host-rewrite |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | HTTPPathModifierType | true | ||
replaceRegexMatch | ReplaceRegexMatch | false | ReplaceRegexMatch defines a path regex rewrite. The path portions matched by the regex pattern are replaced by the defined substitution. https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#envoy-v3-api-field-config-route-v3-routeaction-regex-rewrite Some examples: (1) replaceRegexMatch: pattern: ^/service/([^/]+)(/.)$ substitution: \2/instance/\1 Would transform /service/foo/v1/api into /v1/api/instance/foo. (2) replaceRegexMatch: pattern: one substitution: two Would transform /xxx/one/yyy/one/zzz into /xxx/two/yyy/two/zzz. (3) replaceRegexMatch: pattern: ^(.?)one(.*)$ substitution: \1two\2 Would transform /xxx/one/yyy/one/zzz into /xxx/two/yyy/one/zzz. (3) replaceRegexMatch: pattern: (?i)/xxx/ substitution: /yyy/ Would transform path /aaa/XxX/bbb into /aaa/yyy/bbb (case-insensitive). |
Underlying type: string
HTTPPathModifierType defines the type of path redirect or rewrite.
Appears in:
| Value | Description |
|---|---|
ReplaceRegexMatch | RegexHTTPPathModifier This type of modifier indicates that the portions of the path that match the specified regex would be substituted with the specified substitution value https://www.envoyproxy.io/docs/envoy/latest/api-v3/type/matcher/v3/regex.proto#type-matcher-v3-regexmatchandsubstitute |
HTTPRouteFilter is a custom Envoy Gateway HTTPRouteFilter which provides extended traffic processing options such as path regex rewrite, direct response and more.
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | HTTPRouteFilter | ||
metadata | ObjectMeta | true | Refer to Kubernetes API documentation for fields of metadata. | |
spec | HTTPRouteFilterSpec | true | Spec defines the desired state of HTTPRouteFilter. |
HTTPRouteFilterSpec defines the desired state of HTTPRouteFilter.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
urlRewrite | HTTPURLRewriteFilter | false | ||
directResponse | HTTPDirectResponseFilter | false |
Underlying type: integer
HTTPStatus defines the http status code.
Appears in:
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
connectionIdleTimeout | Duration | false | The idle timeout for an HTTP connection. Idle time is defined as a period in which there are no active requests in the connection. Default: 1 hour. | |
maxConnectionDuration | Duration | false | The maximum duration of an HTTP connection. Default: unlimited. | |
requestTimeout | Duration | false | RequestTimeout is the time until which entire response is received from the upstream. |
HTTPURLRewriteFilter define rewrites of HTTP URL components such as path and host
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
hostname | HTTPHostnameModifier | false | Hostname is the value to be used to replace the Host header value during forwarding. | |
path | HTTPPathModifier | false | Path defines a path rewrite. |
HTTPWasmCodeSource defines the HTTP URL containing the Wasm code.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
url | string | true | URL is the URL containing the Wasm code. | |
sha256 | string | false | SHA256 checksum that will be used to verify the Wasm code. If not specified, Envoy Gateway will not verify the downloaded Wasm code. kubebuilder:validation:Pattern= ^[a-f0-9]\{64\}$ |
Header defines the header hashing configuration for consistent hash based load balancing.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | true | Name of the header to hash. |
HeaderMatch defines the match attributes within the HTTP Headers of the request.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | HeaderMatchType | false | Exact | Type specifies how to match against the value of the header. |
name | string | true | Name of the HTTP header. | |
value | string | false | Value within the HTTP header. Due to the case-insensitivity of header names, “foo” and “Foo” are considered equivalent. Do not set this field when Type=“Distinct”, implying matching on any/all unique values within the header. | |
invert | boolean | false | false | Invert specifies whether the value match result will be inverted. Do not set this field when Type=“Distinct”, implying matching on any/all unique values within the header. |
Underlying type: string
HeaderMatchType specifies the semantics of how HTTP header values should be compared. Valid HeaderMatchType values are “Exact”, “RegularExpression”, and “Distinct”.
Appears in:
| Value | Description |
|---|---|
Exact | HeaderMatchExact matches the exact value of the Value field against the value of the specified HTTP Header. |
RegularExpression | HeaderMatchRegularExpression matches a regular expression against the value of the specified HTTP Header. The regex string must adhere to the syntax documented in https://github.com/google/re2/wiki/Syntax. |
Distinct | HeaderMatchDistinct matches any and all possible unique values encountered in the specified HTTP Header. Note that each unique value will receive its own rate limit bucket. Note: This is only supported for Global Rate Limits. |
HeaderSettings provides configuration options for headers on the listener.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
enableEnvoyHeaders | boolean | false | EnableEnvoyHeaders configures Envoy Proxy to add the “X-Envoy-” headers to requests and responses. | |
disableRateLimitHeaders | boolean | false | DisableRateLimitHeaders configures Envoy Proxy to omit the “X-RateLimit-” response headers when rate limiting is enabled. | |
xForwardedClientCert | XForwardedClientCert | false | XForwardedClientCert configures how Envoy Proxy handle the x-forwarded-client-cert (XFCC) HTTP header. x-forwarded-client-cert (XFCC) is an HTTP header used to forward the certificate information of part or all of the clients or proxies that a request has flowed through, on its way from the client to the server. Envoy proxy may choose to sanitize/append/forward the XFCC header before proxying the request. If not set, the default behavior is sanitizing the XFCC header. | |
withUnderscoresAction | WithUnderscoresAction | false | WithUnderscoresAction configures the action to take when an HTTP header with underscores is encountered. The default action is to reject the request. | |
preserveXRequestID | boolean | false | PreserveXRequestID configures Envoy to keep the X-Request-ID header if passed for a request that is edge (Edge request is the request from external clients to front Envoy) and not reset it, which is the current Envoy behaviour. It defaults to false. | |
earlyRequestHeaders | HTTPHeaderFilter | false | EarlyRequestHeaders defines settings for early request header modification, before envoy performs routing, tracing and built-in header manipulation. |
HealthCheck configuration to decide which endpoints are healthy and can be used for routing.
Note: Once the overall health of the backendRef drops below 50% (e.g. a backendRef having 10 endpoints with more than 5 unhealthy endpoints), Envoy will disregard health status and balance across all endpoints. This is called “panic mode”. It’s designed to prevent a situation in which host failures cascade throughout the cluster as load increases.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
active | ActiveHealthCheck | false | Active health check configuration | |
passive | PassiveHealthCheck | false | Passive passive check configuration |
HealthCheckSettings provides HealthCheck configuration on the HTTP/HTTPS listener.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
path | string | true | Path specifies the HTTP path to match on for health check requests. |
IPEndpoint describes TCP/UDP socket address, corresponding to Envoy’s Socket Address https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/core/v3/address.proto#config-core-v3-socketaddress
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
address | string | true | Address defines the IP address of the backend endpoint. Supports both IPv4 and IPv6 addresses. | |
port | integer | true | Port defines the port of the backend endpoint. |
Underlying type: string
IPFamily defines the IP family to use for the Envoy proxy.
Appears in:
| Value | Description |
|---|---|
IPv4 | IPv4 defines the IPv4 family. |
IPv6 | IPv6 defines the IPv6 family. |
DualStack | DualStack defines the dual-stack family. When set to DualStack, Envoy proxy will listen on both IPv4 and IPv6 addresses for incoming client traffic, enabling support for both IP protocol versions. |
Underlying type: string
ImagePullPolicy defines the policy to use when pulling an OIC image.
Appears in:
| Value | Description |
|---|---|
IfNotPresent | ImagePullPolicyIfNotPresent will only pull the image if it does not already exist in the EG cache. |
Always | ImagePullPolicyAlways will pull the image when the EnvoyExtension resource version changes. Note: EG does not update the Wasm module every time an Envoy proxy requests the Wasm module. |
ImageWasmCodeSource defines the OCI image containing the Wasm code.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
url | string | true | URL is the URL of the OCI image. URL can be in the format of registry/image:tag or registry/image@sha256:digest. | |
sha256 | string | false | SHA256 checksum that will be used to verify the OCI image. It must match the digest of the OCI image. If not specified, Envoy Gateway will not verify the downloaded OCI image. kubebuilder:validation:Pattern= ^[a-f0-9]\{64\}$ | |
pullSecretRef | SecretObjectReference | false | PullSecretRef is a reference to the secret containing the credentials to pull the image. Only support Kubernetes Secret resource from the same namespace. |
Underlying type: string
InfrastructureProviderType defines the types of custom infrastructure providers supported by Envoy Gateway.
Appears in:
| Value | Description |
|---|---|
Host | InfrastructureProviderTypeHost defines the “Host” provider. |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
TerminateConnection | |
TerminateStream |
JSONPatchOperation defines the JSON Patch Operation as defined in https://datatracker.ietf.org/doc/html/rfc6902
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
op | JSONPatchOperationType | true | Op is the type of operation to perform | |
path | string | false | Path is a JSONPointer expression. Refer to https://datatracker.ietf.org/doc/html/rfc6901 for more details. It specifies the location of the target document/field where the operation will be performed | |
jsonPath | string | false | JSONPath is a JSONPath expression. Refer to https://datatracker.ietf.org/doc/rfc9535/ for more details. It produces one or more JSONPointer expressions based on the given JSON document. If no JSONPointer is found, it will result in an error. If the ‘Path’ property is also set, it will be appended to the resulting JSONPointer expressions from the JSONPath evaluation. This is useful when creating a property that does not yet exist in the JSON document. The final JSONPointer expressions specifies the locations in the target document/field where the operation will be applied. | |
from | string | false | From is the source location of the value to be copied or moved. Only valid for move or copy operations Refer to https://datatracker.ietf.org/doc/html/rfc6901 for more details. | |
value | JSON | false | Value is the new value of the path location. The value is only used by the add and replace operations. |
Underlying type: string
JSONPatchOperationType specifies the JSON Patch operations that can be performed.
Appears in:
JWT defines the configuration for JSON Web Token (JWT) authentication.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
optional | boolean | true | Optional determines whether a missing JWT is acceptable, defaulting to false if not specified. Note: Even if optional is set to true, JWT authentication will still fail if an invalid JWT is presented. | |
providers | JWTProvider array | true | Providers defines the JSON Web Token (JWT) authentication provider type. When multiple JWT providers are specified, the JWT is considered valid if any of the providers successfully validate the JWT. For additional details, see https://www.envoyproxy.io/docs/envoy/latest/configuration/http/http_filters/jwt_authn_filter.html. |
JWTClaim specifies a claim in a JWT token.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | true | Name is the name of the claim. If it is a nested claim, use a dot (.) separated string as the name to represent the full path to the claim. For example, if the claim is in the “department” field in the “organization” field, the name should be “organization.department”. | |
valueType | JWTClaimValueType | false | String | ValueType is the type of the claim value. Only String and StringArray types are supported for now. |
values | string array | true | Values are the values that the claim must match. If the claim is a string type, the specified value must match exactly. If the claim is a string array type, the specified value must match one of the values in the array. If multiple values are specified, one of the values must match for the rule to match. |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
String | |
StringArray |
JWTExtractor defines a custom JWT token extraction from HTTP request. If specified, Envoy will extract the JWT token from the listed extractors (headers, cookies, or params) and validate each of them. If any value extracted is found to be an invalid JWT, a 401 error will be returned.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
headers | JWTHeaderExtractor array | false | Headers represents a list of HTTP request headers to extract the JWT token from. | |
cookies | string array | false | Cookies represents a list of cookie names to extract the JWT token from. | |
params | string array | false | Params represents a list of query parameters to extract the JWT token from. |
JWTHeaderExtractor defines an HTTP header location to extract JWT token
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | true | Name is the HTTP header name to retrieve the token | |
valuePrefix | string | false | ValuePrefix is the prefix that should be stripped before extracting the token. The format would be used by Envoy like “{ValuePrefix} For example, “Authorization: Bearer |
JWTPrincipal specifies the client identity of a request based on the JWT claims and scopes. At least one of the claims or scopes must be specified. Claims and scopes are And-ed together if both are specified.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
provider | string | true | Provider is the name of the JWT provider that used to verify the JWT token. In order to use JWT claims for authorization, you must configure the JWT authentication with the same provider in the same SecurityPolicy. | |
claims | JWTClaim array | false | Claims are the claims in a JWT token. If multiple claims are specified, all claims must match for the rule to match. For example, if there are two claims: one for the audience and one for the issuer, the rule will match only if both the audience and the issuer match. | |
scopes | JWTScope array | false | Scopes are a special type of claim in a JWT token that represents the permissions of the client. The value of the scopes field should be a space delimited string that is expected in the scope parameter, as defined in RFC 6749: https://datatracker.ietf.org/doc/html/rfc6749#page-23. If multiple scopes are specified, all scopes must match for the rule to match. |
JWTProvider defines how a JSON Web Token (JWT) can be verified.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | true | Name defines a unique name for the JWT provider. A name can have a variety of forms, including RFC1123 subdomains, RFC 1123 labels, or RFC 1035 labels. | |
issuer | string | false | Issuer is the principal that issued the JWT and takes the form of a URL or email address. For additional details, see https://tools.ietf.org/html/rfc7519#section-4.1.1 for URL format and https://rfc-editor.org/rfc/rfc5322.html for email format. If not provided, the JWT issuer is not checked. | |
audiences | string array | false | Audiences is a list of JWT audiences allowed access. For additional details, see https://tools.ietf.org/html/rfc7519#section-4.1.3. If not provided, JWT audiences are not checked. | |
remoteJWKS | RemoteJWKS | true | RemoteJWKS defines how to fetch and cache JSON Web Key Sets (JWKS) from a remote HTTP/HTTPS endpoint. | |
claimToHeaders | ClaimToHeader array | false | ClaimToHeaders is a list of JWT claims that must be extracted into HTTP request headers For examples, following config: The claim must be of type; string, int, double, bool. Array type claims are not supported | |
recomputeRoute | boolean | false | RecomputeRoute clears the route cache and recalculates the routing decision. This field must be enabled if the headers generated from the claim are used for route matching decisions. If the recomputation selects a new route, features targeting the new matched route will be applied. | |
extractFrom | JWTExtractor | false | ExtractFrom defines different ways to extract the JWT token from HTTP request. If empty, it defaults to extract JWT token from the Authorization HTTP request header using Bearer schema or access_token from query parameters. |
Underlying type: string
Appears in:
KubernetesContainerSpec defines the desired state of the Kubernetes container resource.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
env | EnvVar array | false | List of environment variables to set in the container. | |
resources | ResourceRequirements | false | Resources required by this container. More info: https://kubernetes.io/docs/concepts/configuration/manage-resources-containers/ | |
securityContext | SecurityContext | false | SecurityContext defines the security options the container should be run with. If set, the fields of SecurityContext override the equivalent fields of PodSecurityContext. More info: https://kubernetes.io/docs/tasks/configure-pod-container/security-context/ | |
image | string | false | Image specifies the EnvoyProxy container image to be used, instead of the default image. | |
volumeMounts | VolumeMount array | false | VolumeMounts are volumes to mount into the container’s filesystem. Cannot be updated. |
KubernetesDaemonSetSpec defines the desired state of the Kubernetes daemonset resource.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
patch | KubernetesPatchSpec | false | Patch defines how to perform the patch operation to daemonset | |
strategy | DaemonSetUpdateStrategy | false | The daemonset strategy to use to replace existing pods with new ones. | |
pod | KubernetesPodSpec | false | Pod defines the desired specification of pod. | |
container | KubernetesContainerSpec | false | Container defines the desired specification of main container. | |
name | string | false | Name of the daemonSet. When unset, this defaults to an autogenerated name. |
KubernetesDeployMode holds configuration for how to deploy managed resources such as the Envoy Proxy data plane fleet.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | KubernetesDeployModeType | false | ControllerNamespace | Type indicates what deployment mode to use. “ControllerNamespace” and “GatewayNamespace” are currently supported. By default, when this field is unset or empty, Envoy Gateway will deploy Envoy Proxy fleet in the Controller namespace. |
Underlying type: string
KubernetesDeployModeType defines the type of KubernetesDeployMode
Appears in:
KubernetesDeploymentSpec defines the desired state of the Kubernetes deployment resource.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
patch | KubernetesPatchSpec | false | Patch defines how to perform the patch operation to deployment | |
replicas | integer | false | Replicas is the number of desired pods. Defaults to 1. | |
strategy | DeploymentStrategy | false | The deployment strategy to use to replace existing pods with new ones. | |
pod | KubernetesPodSpec | false | Pod defines the desired specification of pod. | |
container | KubernetesContainerSpec | false | Container defines the desired specification of main container. | |
initContainers | Container array | false | List of initialization containers belonging to the pod. More info: https://kubernetes.io/docs/concepts/workloads/pods/init-containers/ | |
name | string | false | Name of the deployment. When unset, this defaults to an autogenerated name. |
KubernetesHorizontalPodAutoscalerSpec defines Kubernetes Horizontal Pod Autoscaler settings of Envoy Proxy Deployment.
When HPA is enabled, it is recommended that the value in KubernetesDeploymentSpec.replicas be removed, otherwise
Envoy Gateway will revert back to this value every time reconciliation occurs.
See k8s.io.autoscaling.v2.HorizontalPodAutoScalerSpec.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
minReplicas | integer | false | minReplicas is the lower limit for the number of replicas to which the autoscaler can scale down. It defaults to 1 replica. | |
maxReplicas | integer | true | maxReplicas is the upper limit for the number of replicas to which the autoscaler can scale up. It cannot be less that minReplicas. | |
metrics | MetricSpec array | false | metrics contains the specifications for which to use to calculate the desired replica count (the maximum replica count across all metrics will be used). If left empty, it defaults to being based on CPU utilization with average on 80% usage. | |
behavior | HorizontalPodAutoscalerBehavior | false | behavior configures the scaling behavior of the target in both Up and Down directions (scaleUp and scaleDown fields respectively). If not set, the default HPAScalingRules for scale up and scale down are used. See k8s.io.autoscaling.v2.HorizontalPodAutoScalerBehavior. | |
patch | KubernetesPatchSpec | false | Patch defines how to perform the patch operation to the HorizontalPodAutoscaler |
KubernetesPatchSpec defines how to perform the patch operation.
Note that value can be an in-line YAML document, as can be seen in e.g. (the example of patching the Envoy proxy Deployment)[https://gateway.envoyproxy.io/docs/tasks/operations/customize-envoyproxy/#patching-deployment-for-envoyproxy].
Note also that, currently, strings containing literal JSON are rejected.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | MergeType | false | Type is the type of merge operation to perform By default, StrategicMerge is used as the patch type. | |
value | JSON | true | Object contains the raw configuration for merged object |
KubernetesPodDisruptionBudgetSpec defines Kubernetes PodDisruptionBudget settings of Envoy Proxy Deployment.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
minAvailable | integer | false | MinAvailable specifies the minimum number of pods that must be available at all times during voluntary disruptions, such as node drains or updates. This setting ensures that your envoy proxy maintains a certain level of availability and resilience during maintenance operations. | |
patch | KubernetesPatchSpec | false | Patch defines how to perform the patch operation to the PodDisruptionBudget |
KubernetesPodSpec defines the desired state of the Kubernetes pod resource.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
annotations | object (keys:string, values:string) | false | Annotations are the annotations that should be appended to the pods. By default, no pod annotations are appended. | |
labels | object (keys:string, values:string) | false | Labels are the additional labels that should be tagged to the pods. By default, no additional pod labels are tagged. | |
securityContext | PodSecurityContext | false | SecurityContext holds pod-level security attributes and common container settings. Optional: Defaults to empty. See type description for default values of each field. | |
affinity | Affinity | false | If specified, the pod’s scheduling constraints. | |
tolerations | Toleration array | false | If specified, the pod’s tolerations. | |
volumes | Volume array | false | Volumes that can be mounted by containers belonging to the pod. More info: https://kubernetes.io/docs/concepts/storage/volumes | |
imagePullSecrets | LocalObjectReference array | false | ImagePullSecrets is an optional list of references to secrets in the same namespace to use for pulling any of the images used by this PodSpec. If specified, these secrets will be passed to individual puller implementations for them to use. More info: https://kubernetes.io/docs/concepts/containers/images#specifying-imagepullsecrets-on-a-pod | |
nodeSelector | object (keys:string, values:string) | false | NodeSelector is a selector which must be true for the pod to fit on a node. Selector which must match a node’s labels for the pod to be scheduled on that node. More info: https://kubernetes.io/docs/concepts/configuration/assign-pod-node/ | |
topologySpreadConstraints | TopologySpreadConstraint array | false | TopologySpreadConstraints describes how a group of pods ought to spread across topology domains. Scheduler will schedule pods in a way which abides by the constraints. All topologySpreadConstraints are ANDed. |
KubernetesServiceSpec defines the desired state of the Kubernetes service resource.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
annotations | object (keys:string, values:string) | false | Annotations that should be appended to the service. By default, no annotations are appended. | |
labels | object (keys:string, values:string) | false | Labels that should be appended to the service. By default, no labels are appended. | |
type | ServiceType | false | LoadBalancer | Type determines how the Service is exposed. Defaults to LoadBalancer. Valid options are ClusterIP, LoadBalancer and NodePort. “LoadBalancer” means a service will be exposed via an external load balancer (if the cloud provider supports it). “ClusterIP” means a service will only be accessible inside the cluster, via the cluster IP. “NodePort” means a service will be exposed on a static Port on all Nodes of the cluster. |
loadBalancerClass | string | false | LoadBalancerClass, when specified, allows for choosing the LoadBalancer provider implementation if more than one are available or is otherwise expected to be specified | |
allocateLoadBalancerNodePorts | boolean | false | AllocateLoadBalancerNodePorts defines if NodePorts will be automatically allocated for services with type LoadBalancer. Default is “true”. It may be set to “false” if the cluster load-balancer does not rely on NodePorts. If the caller requests specific NodePorts (by specifying a value), those requests will be respected, regardless of this field. This field may only be set for services with type LoadBalancer and will be cleared if the type is changed to any other type. | |
loadBalancerSourceRanges | string array | false | LoadBalancerSourceRanges defines a list of allowed IP addresses which will be configured as firewall rules on the platform providers load balancer. This is not guaranteed to be working as it happens outside of kubernetes and has to be supported and handled by the platform provider. This field may only be set for services with type LoadBalancer and will be cleared if the type is changed to any other type. | |
loadBalancerIP | string | false | LoadBalancerIP defines the IP Address of the underlying load balancer service. This field may be ignored if the load balancer provider does not support this feature. This field has been deprecated in Kubernetes, but it is still used for setting the IP Address in some cloud providers such as GCP. | |
externalTrafficPolicy | ServiceExternalTrafficPolicy | false | Local | ExternalTrafficPolicy determines the externalTrafficPolicy for the Envoy Service. Valid options are Local and Cluster. Default is “Local”. “Local” means traffic will only go to pods on the node receiving the traffic. “Cluster” means connections are loadbalanced to all pods in the cluster. |
patch | KubernetesPatchSpec | false | Patch defines how to perform the patch operation to the service | |
name | string | false | Name of the service. When unset, this defaults to an autogenerated name. |
KubernetesWatchMode holds the configuration for which input resources to watch and reconcile.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | KubernetesWatchModeType | true | Type indicates what watch mode to use. KubernetesWatchModeTypeNamespaces and KubernetesWatchModeTypeNamespaceSelector are currently supported By default, when this field is unset or empty, Envoy Gateway will watch for input namespaced resources from all namespaces. | |
namespaces | string array | true | Namespaces holds the list of namespaces that Envoy Gateway will watch for namespaced scoped resources such as Gateway, HTTPRoute and Service. Note that Envoy Gateway will continue to reconcile relevant cluster scoped resources such as GatewayClass that it is linked to. Precisely one of Namespaces and NamespaceSelector must be set. | |
namespaceSelector | LabelSelector | true | NamespaceSelector holds the label selector used to dynamically select namespaces. Envoy Gateway will watch for namespaces matching the specified label selector. Precisely one of Namespaces and NamespaceSelector must be set. |
Underlying type: string
KubernetesWatchModeType defines the type of KubernetesWatchMode
Appears in:
LeaderElection defines the desired leader election settings.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
leaseDuration | Duration | true | LeaseDuration defines the time non-leader contenders will wait before attempting to claim leadership. It’s based on the timestamp of the last acknowledged signal. The default setting is 15 seconds. | |
renewDeadline | Duration | true | RenewDeadline represents the time frame within which the current leader will attempt to renew its leadership status before relinquishing its position. The default setting is 10 seconds. | |
retryPeriod | Duration | true | RetryPeriod denotes the interval at which LeaderElector clients should perform action retries. The default setting is 2 seconds. | |
disable | boolean | true | Disable provides the option to turn off leader election, which is enabled by default. |
LiteralCustomTag adds hard-coded value to each span.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
value | string | true | Value defines the hard-coded value to add to each span. |
LoadBalancer defines the load balancer policy to be applied.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | LoadBalancerType | true | Type decides the type of Load Balancer policy. Valid LoadBalancerType values are “ConsistentHash”, “LeastRequest”, “Random”, “RoundRobin”. | |
consistentHash | ConsistentHash | false | ConsistentHash defines the configuration when the load balancer type is set to ConsistentHash | |
slowStart | SlowStart | false | SlowStart defines the configuration related to the slow start load balancer policy. If set, during slow start window, traffic sent to the newly added hosts will gradually increase. Currently this is only supported for RoundRobin and LeastRequest load balancers |
Underlying type: string
LoadBalancerType specifies the types of LoadBalancer.
Appears in:
| Value | Description |
|---|---|
ConsistentHash | ConsistentHashLoadBalancerType load balancer policy. |
LeastRequest | LeastRequestLoadBalancerType load balancer policy. |
Random | RandomLoadBalancerType load balancer policy. |
RoundRobin | RoundRobinLoadBalancerType load balancer policy. |
LocalRateLimit defines local rate limit configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
rules | RateLimitRule array | false | Rules are a list of RateLimit selectors and limits. If a request matches multiple rules, the strictest limit is applied. For example, if a request matches two rules, one with 10rps and one with 20rps, the final limit will be based on the rule with 10rps. |
Underlying type: string
LogLevel defines a log level for Envoy Gateway and EnvoyProxy system logs.
Appears in:
| Value | Description |
|---|---|
debug | LogLevelDebug defines the “debug” logging level. |
info | LogLevelInfo defines the “Info” logging level. |
warn | LogLevelWarn defines the “Warn” logging level. |
error | LogLevelError defines the “Error” logging level. |
Lua defines a Lua extension Only one of Inline or ValueRef must be set
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | LuaValueType | true | Inline | Type is the type of method to use to read the Lua value. Valid values are Inline and ValueRef, default is Inline. |
inline | string | false | Inline contains the source code as an inline string. | |
valueRef | LocalObjectReference | false | ValueRef has the source code specified as a local object reference. Only a reference to ConfigMap is supported. The value of key lua in the ConfigMap will be used.If the key is not found, the first value in the ConfigMap will be used. |
Underlying type: string
LuaValueType defines the types of values for Lua supported by Envoy Gateway.
Appears in:
| Value | Description |
|---|---|
Inline | LuaValueTypeInline defines the “Inline” Lua type. |
ValueRef | LuaValueTypeValueRef defines the “ValueRef” Lua type. |
Underlying type: string
MergeType defines the type of merge operation
Appears in:
| Value | Description |
|---|---|
StrategicMerge | StrategicMerge indicates a strategic merge patch type |
JSONMerge | JSONMerge indicates a JSON merge patch type |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
OpenTelemetry |
OIDC defines the configuration for the OpenID Connect (OIDC) authentication.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
provider | OIDCProvider | true | The OIDC Provider configuration. | |
clientID | string | true | The client ID to be used in the OIDC Authentication Request. | |
clientSecret | SecretObjectReference | true | The Kubernetes secret which contains the OIDC client secret to be used in the Authentication Request. This is an Opaque secret. The client secret should be stored in the key “client-secret”. | |
cookieNames | OIDCCookieNames | false | The optional cookie name overrides to be used for Bearer and IdToken cookies in the Authentication Request. If not specified, uses a randomly generated suffix | |
cookieDomain | string | false | The optional domain to set the access and ID token cookies on. If not set, the cookies will default to the host of the request, not including the subdomains. If set, the cookies will be set on the specified domain and all subdomains. This means that requests to any subdomain will not require reauthentication after users log in to the parent domain. | |
scopes | string array | false | The OIDC scopes to be used in the Authentication Request. The “openid” scope is always added to the list of scopes if not already specified. | |
resources | string array | false | The OIDC resources to be used in the Authentication Request. | |
redirectURL | string | true | The redirect URL to be used in the OIDC Authentication Request. If not specified, uses the default redirect URI “%REQ(x-forwarded-proto)%://%REQ(:authority)%/oauth2/callback” | |
logoutPath | string | true | The path to log a user out, clearing their credential cookies. If not specified, uses a default logout path “/logout” | |
forwardAccessToken | boolean | false | ForwardAccessToken indicates whether the Envoy should forward the access token via the Authorization header Bearer scheme to the upstream. If not specified, defaults to false. | |
defaultTokenTTL | Duration | false | DefaultTokenTTL is the default lifetime of the id token and access token. Please note that Envoy will always use the expiry time from the response of the authorization server if it is provided. This field is only used when the expiry time is not provided by the authorization. If not specified, defaults to 0. In this case, the “expires_in” field in the authorization response must be set by the authorization server, or the OAuth flow will fail. | |
refreshToken | boolean | false | RefreshToken indicates whether the Envoy should automatically refresh the id token and access token when they expire. When set to true, the Envoy will use the refresh token to get a new id token and access token when they expire. If not specified, defaults to false. | |
defaultRefreshTokenTTL | Duration | false | DefaultRefreshTokenTTL is the default lifetime of the refresh token. This field is only used when the exp (expiration time) claim is omitted in the refresh token or the refresh token is not JWT. If not specified, defaults to 604800s (one week). Note: this field is only applicable when the “refreshToken” field is set to true. |
OIDCCookieNames defines the names of cookies to use in the Envoy OIDC filter.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
accessToken | string | false | The name of the cookie used to store the AccessToken in the Authentication Request. If not specified, defaults to “AccessToken-(randomly generated uid)” | |
idToken | string | false | The name of the cookie used to store the IdToken in the Authentication Request. If not specified, defaults to “IdToken-(randomly generated uid)” |
OIDCProvider defines the OIDC Provider configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. | |
issuer | string | true | The OIDC Provider’s issuer identifier. Issuer MUST be a URI RFC 3986 [RFC3986] with a scheme component that MUST be https, a host component, and optionally, port and path components and no query or fragment components. | |
authorizationEndpoint | string | false | The OIDC Provider’s authorization endpoint. If not provided, EG will try to discover it from the provider’s Well-Known Configuration Endpoint. | |
tokenEndpoint | string | false | The OIDC Provider’s token endpoint. If not provided, EG will try to discover it from the provider’s Well-Known Configuration Endpoint. |
OpenTelemetryEnvoyProxyAccessLog defines the OpenTelemetry access log sink.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. | |
host | string | false | Host define the extension service hostname. Deprecated: Use BackendRefs instead. | |
port | integer | false | 4317 | Port defines the port the extension service is exposed on. Deprecated: Use BackendRefs instead. |
resources | object (keys:string, values:string) | false | Resources is a set of labels that describe the source of a log entry, including envoy node info. It’s recommended to follow semantic conventions. |
Underlying type: string
Origin is defined by the scheme (protocol), hostname (domain), and port of the URL used to access it. The hostname can be “precise” which is just the domain name or “wildcard” which is a domain name prefixed with a single wildcard label such as “*.example.com”. In addition to that a single wildcard (with or without scheme) can be configured to match any origin.
For example, the following are valid origins:
Appears in:
PassiveHealthCheck defines the configuration for passive health checks in the context of Envoy’s Outlier Detection, see https://www.envoyproxy.io/docs/envoy/latest/intro/arch_overview/upstream/outlier
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
splitExternalLocalOriginErrors | boolean | false | false | SplitExternalLocalOriginErrors enables splitting of errors between external and local origin. |
interval | Duration | false | 3s | Interval defines the time between passive health checks. |
consecutiveLocalOriginFailures | integer | false | 5 | ConsecutiveLocalOriginFailures sets the number of consecutive local origin failures triggering ejection. Parameter takes effect only when split_external_local_origin_errors is set to true. |
consecutiveGatewayErrors | integer | false | 0 | ConsecutiveGatewayErrors sets the number of consecutive gateway errors triggering ejection. |
consecutive5XxErrors | integer | false | 5 | Consecutive5xxErrors sets the number of consecutive 5xx errors triggering ejection. |
baseEjectionTime | Duration | false | 30s | BaseEjectionTime defines the base duration for which a host will be ejected on consecutive failures. |
maxEjectionPercent | integer | false | 10 | MaxEjectionPercent sets the maximum percentage of hosts in a cluster that can be ejected. |
Underlying type: string
PathEscapedSlashAction determines the action for requests that contain %2F, %2f, %5C, or %5c sequences in the URI path.
Appears in:
| Value | Description |
|---|---|
KeepUnchanged | KeepUnchangedAction keeps escaped slashes as they arrive without changes |
RejectRequest | RejectRequestAction rejects client requests containing escaped slashes with a 400 status. gRPC requests will be rejected with the INTERNAL (13) error code. The “httpN.downstream_rq_failed_path_normalization” counter is incremented for each rejected request. |
UnescapeAndRedirect | UnescapeAndRedirect unescapes %2F and %5C sequences and redirects to the new path if these sequences were present. Redirect occurs after path normalization and merge slashes transformations if they were configured. gRPC requests will be rejected with the INTERNAL (13) error code. This option minimizes possibility of path confusion exploits by forcing request with unescaped slashes to traverse all parties: downstream client, intermediate proxies, Envoy and upstream server. The “httpN.downstream_rq_redirected_with_normalized_path” counter is incremented for each redirected request. |
UnescapeAndForward | UnescapeAndForward unescapes %2F and %5C sequences and forwards the request. Note: this option should not be enabled if intermediaries perform path based access control as it may lead to path confusion vulnerabilities. |
PathSettings provides settings that managing how the incoming path set by clients is handled.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
escapedSlashesAction | PathEscapedSlashAction | false | EscapedSlashesAction determines how %2f, %2F, %5c, or %5C sequences in the path URI should be handled. The default is UnescapeAndRedirect. | |
disableMergeSlashes | boolean | false | DisableMergeSlashes allows disabling the default configuration of merging adjacent slashes in the path. Note that slash merging is not part of the HTTP spec and is provided for convenience. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
timeout | Duration | false | Timeout is the timeout per retry attempt. | |
backOff | BackOffPolicy | false | Backoff is the backoff policy to be applied per retry attempt. gateway uses a fully jittered exponential back-off algorithm for retries. For additional details, see https://www.envoyproxy.io/docs/envoy/latest/configuration/http/http_filters/router_filter#config-http-filters-router-x-envoy-max-retries |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
targetRef | LocalPolicyTargetReferenceWithSectionName | true | TargetRef is the name of the resource this policy is being attached to. This policy and the TargetRef MUST be in the same namespace for this Policy to have effect Deprecated: use targetRefs/targetSelectors instead | |
targetRefs | LocalPolicyTargetReferenceWithSectionName array | true | TargetRefs are the names of the Gateway resources this policy is being attached to. | |
targetSelectors | TargetSelector array | true | TargetSelectors allow targeting resources for this policy based on labels |
If there are multiple principal types, all principals must match for the rule to match.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
clientCIDRs | CIDR array | false | ClientCIDRs are the IP CIDR ranges of the client. Valid examples are “192.168.1.0/24” or “2001:db8::/64” If multiple CIDR ranges are specified, one of the CIDR ranges must match the client IP for the rule to match. The client IP is inferred from the X-Forwarded-For header, a custom header, or the proxy protocol. You can use the ClientIPDetection or the EnableProxyProtocol field inthe ClientTrafficPolicy to configure how the client IP is detected. | |
jwt | JWTPrincipal | false | JWT authorize the request based on the JWT claims and scopes. Note: in order to use JWT claims for authorization, you must configure the JWT authentication in the same SecurityPolicy. |
ProcessingModeOptions defines if headers or body should be processed by the external service and which attributes are sent to the processor
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
body | ExtProcBodyProcessingMode | false | Defines body processing mode | |
attributes | string array | false | Defines which attributes are sent to the external processor. Envoy Gateway currently supports only the following attribute prefixes: connection, source, destination, request, response, upstream and xds.route. https://www.envoyproxy.io/docs/envoy/latest/intro/arch_overview/advanced/attributes |
Underlying type: string
ProviderType defines the types of providers supported by Envoy Gateway.
Appears in:
| Value | Description |
|---|---|
Kubernetes | ProviderTypeKubernetes defines the “Kubernetes” provider. |
Custom | ProviderTypeCustom defines the “Custom” provider. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
disable | boolean | true | Disable disables access logging for managed proxies if set to true. | |
settings | ProxyAccessLogSetting array | false | Settings defines accesslog settings for managed proxies. If unspecified, will send default format to stdout. |
ProxyAccessLogFormat defines the format of accesslog. By default accesslogs are written to standard output.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | ProxyAccessLogFormatType | true | Type defines the type of accesslog format. | |
text | string | false | Text defines the text accesslog format, following Envoy accesslog formatting, It’s required when the format type is “Text”. Envoy command operators may be used in the format. The format string documentation provides more information. | |
json | object (keys:string, values:string) | false | JSON is additional attributes that describe the specific event occurrence. Structured format for the envoy access logs. Envoy command operators can be used as values for fields within the Struct. It’s required when the format type is “JSON”. |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
Text | ProxyAccessLogFormatTypeText defines the text accesslog format. |
JSON | ProxyAccessLogFormatTypeJSON defines the JSON accesslog format. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
format | ProxyAccessLogFormat | false | Format defines the format of accesslog. This will be ignored if sink type is ALS. | |
matches | string array | true | Matches defines the match conditions for accesslog in CEL expression. An accesslog will be emitted only when one or more match conditions are evaluated to true. Invalid CEL expressions will be ignored. | |
sinks | ProxyAccessLogSink array | true | Sinks defines the sinks of accesslog. | |
type | ProxyAccessLogType | false | Type defines the component emitting the accesslog, such as Listener and Route. If type not defined, the setting would apply to: (1) All Routes. (2) Listeners if and only if Envoy does not find a matching route for a request. If type is defined, the accesslog settings would apply to the relevant component (as-is). |
ProxyAccessLogSink defines the sink of accesslog.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | ProxyAccessLogSinkType | true | Type defines the type of accesslog sink. | |
als | ALSEnvoyProxyAccessLog | false | ALS defines the gRPC Access Log Service (ALS) sink. | |
file | FileEnvoyProxyAccessLog | false | File defines the file accesslog sink. | |
openTelemetry | OpenTelemetryEnvoyProxyAccessLog | false | OpenTelemetry defines the OpenTelemetry accesslog sink. |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
ALS | ProxyAccessLogSinkTypeALS defines the gRPC Access Log Service (ALS) sink. The service must implement the Envoy gRPC Access Log Service streaming API: https://www.envoyproxy.io/docs/envoy/latest/api-v3/service/accesslog/v3/als.proto |
File | ProxyAccessLogSinkTypeFile defines the file accesslog sink. |
OpenTelemetry | ProxyAccessLogSinkTypeOpenTelemetry defines the OpenTelemetry accesslog sink. When the provider is Kubernetes, EnvoyGateway always sends k8s.namespace.nameand k8s.pod.name as additional attributes. |
Underlying type: string
Appears in:
ProxyBootstrap defines Envoy Bootstrap configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | BootstrapType | false | Replace | Type is the type of the bootstrap configuration, it should be either Replace, Merge, or JSONPatch. If unspecified, it defaults to Replace. |
value | string | false | Value is a YAML string of the bootstrap. | |
jsonPatches | JSONPatchOperation array | true | JSONPatches is an array of JSONPatches to be applied to the default bootstrap. Patches are applied in the order in which they are defined. |
Underlying type: string
ProxyLogComponent defines a component that supports a configured logging level.
Appears in:
| Value | Description |
|---|---|
default | LogComponentDefault defines the default logging component. See more details: https://www.envoyproxy.io/docs/envoy/latest/operations/cli#cmdoption-l |
upstream | LogComponentUpstream defines the “upstream” logging component. |
http | LogComponentHTTP defines the “http” logging component. |
connection | LogComponentConnection defines the “connection” logging component. |
admin | LogComponentAdmin defines the “admin” logging component. |
client | LogComponentClient defines the “client” logging component. |
filter | LogComponentFilter defines the “filter” logging component. |
main | LogComponentMain defines the “main” logging component. |
router | LogComponentRouter defines the “router” logging component. |
runtime | LogComponentRuntime defines the “runtime” logging component. |
ProxyLogging defines logging parameters for managed proxies.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
level | object (keys:ProxyLogComponent, values:LogLevel) | true | { default:warn } | Level is a map of logging level per component, where the component is the key and the log level is the value. If unspecified, defaults to “default: warn”. |
ProxyMetricSink defines the sink of metrics. Default metrics sink is OpenTelemetry.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | MetricSinkType | true | OpenTelemetry | Type defines the metric sink type. EG currently only supports OpenTelemetry. |
openTelemetry | ProxyOpenTelemetrySink | false | OpenTelemetry defines the configuration for OpenTelemetry sink. It’s required if the sink type is OpenTelemetry. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
prometheus | ProxyPrometheusProvider | true | Prometheus defines the configuration for Admin endpoint /stats/prometheus. | |
sinks | ProxyMetricSink array | true | Sinks defines the metric sinks where metrics are sent to. | |
matches | StringMatch array | true | Matches defines configuration for selecting specific metrics instead of generating all metrics stats that are enabled by default. This helps reduce CPU and memory overhead in Envoy, but eliminating some stats may after critical functionality. Here are the stats that we strongly recommend not disabling: cluster_manager.warming_clusters, cluster.<cluster_name>.membership_total,cluster.<cluster_name>.membership_healthy,cluster.<cluster_name>.membership_degraded,reference https://github.com/envoyproxy/envoy/issues/9856,https://github.com/envoyproxy/envoy/issues/14610 | |
enableVirtualHostStats | boolean | false | EnableVirtualHostStats enables envoy stat metrics for virtual hosts. | |
enablePerEndpointStats | boolean | false | EnablePerEndpointStats enables per endpoint envoy stats metrics. Please use with caution. | |
enableRequestResponseSizesStats | boolean | false | EnableRequestResponseSizesStats enables publishing of histograms tracking header and body sizes of requests and responses. |
ProxyOpenTelemetrySink defines the configuration for OpenTelemetry sink.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. | |
host | string | false | Host define the service hostname. Deprecated: Use BackendRefs instead. | |
port | integer | false | 4317 | Port defines the port the service is exposed on. Deprecated: Use BackendRefs instead. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
disable | boolean | true | Disable the Prometheus endpoint. | |
compression | Compression | false | Configure the compression on Prometheus endpoint. Compression is useful in situations when bandwidth is scarce and large payloads can be effectively compressed at the expense of higher CPU load. |
ProxyProtocol defines the configuration related to the proxy protocol when communicating with the backend.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
version | ProxyProtocolVersion | true | Version of ProxyProtol Valid ProxyProtocolVersion values are “V1” “V2” |
Underlying type: string
ProxyProtocolVersion defines the version of the Proxy Protocol to use.
Appears in:
| Value | Description |
|---|---|
V1 | ProxyProtocolVersionV1 is the PROXY protocol version 1 (human readable format). |
V2 | ProxyProtocolVersionV2 is the PROXY protocol version 2 (binary format). |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
accessLog | ProxyAccessLog | false | AccessLogs defines accesslog parameters for managed proxies. If unspecified, will send default format to stdout. | |
tracing | ProxyTracing | false | Tracing defines tracing configuration for managed proxies. If unspecified, will not send tracing data. | |
metrics | ProxyMetrics | true | Metrics defines metrics configuration for managed proxies. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
samplingRate | integer | false | 100 | SamplingRate controls the rate at which traffic will be selected for tracing if no prior sampling decision has been made. Defaults to 100, valid values [0-100]. 100 indicates 100% sampling. |
customTags | object (keys:string, values:CustomTag) | true | CustomTags defines the custom tags to add to each span. If provider is kubernetes, pod name and namespace are added by default. | |
provider | TracingProvider | true | Provider defines the tracing provider. |
RateLimit defines the configuration associated with the Rate Limit Service used for Global Rate Limiting.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backend | RateLimitDatabaseBackend | true | Backend holds the configuration associated with the database backend used by the rate limit service to store state associated with global ratelimiting. | |
timeout | Duration | false | Timeout specifies the timeout period for the proxy to access the ratelimit server If not set, timeout is 20ms. | |
failClosed | boolean | true | FailClosed is a switch used to control the flow of traffic when the response from the ratelimit server cannot be obtained. If FailClosed is false, let the traffic pass, otherwise, don’t let the traffic pass and return 500. If not set, FailClosed is False. | |
telemetry | RateLimitTelemetry | false | Telemetry defines telemetry configuration for RateLimit. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
request | RateLimitCostSpecifier | false | Request specifies the number to reduce the rate limit counters on the request path. If this is not specified, the default behavior is to reduce the rate limit counters by 1. When Envoy receives a request that matches the rule, it tries to reduce the rate limit counters by the specified number. If the counter doesn’t have enough capacity, the request is rate limited. | |
response | RateLimitCostSpecifier | false | Response specifies the number to reduce the rate limit counters after the response is sent back to the client or the request stream is closed. The cost is used to reduce the rate limit counters for the matching requests. Since the reduction happens after the request stream is complete, the rate limit won’t be enforced for the current request, but for the subsequent matching requests. This is optional and if not specified, the rate limit counters are not reduced on the response path. Currently, this is only supported for HTTP Global Rate Limits. |
Underlying type: string
RateLimitCostFrom specifies the source of the rate limit cost. Valid RateLimitCostType values are “Number” and “Metadata”.
Appears in:
| Value | Description |
|---|---|
Number | RateLimitCostFromNumber specifies the rate limit cost to be a fixed number. |
Metadata | RateLimitCostFromMetadata specifies the rate limit cost to be retrieved from the per-request dynamic metadata. |
RateLimitCostMetadata specifies the filter metadata to retrieve the usage number from.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
namespace | string | true | Namespace is the namespace of the dynamic metadata. | |
key | string | true | Key is the key to retrieve the usage number from the filter metadata. |
RateLimitCostSpecifier specifies where the Envoy retrieves the number to reduce the rate limit counters.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
from | RateLimitCostFrom | true | From specifies where to get the rate limit cost. Currently, only “Number” and “Metadata” are supported. | |
number | integer | false | Number specifies the fixed usage number to reduce the rate limit counters. Using zero can be used to only check the rate limit counters without reducing them. | |
metadata | RateLimitCostMetadata | false | Refer to Kubernetes API documentation for fields of metadata. |
RateLimitDatabaseBackend defines the configuration associated with the database backend used by the rate limit service.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | RateLimitDatabaseBackendType | true | Type is the type of database backend to use. Supported types are: * Redis: Connects to a Redis database. | |
redis | RateLimitRedisSettings | false | Redis defines the settings needed to connect to a Redis database. |
Underlying type: string
RateLimitDatabaseBackendType specifies the types of database backend to be used by the rate limit service.
Appears in:
| Value | Description |
|---|---|
Redis | RedisBackendType uses a redis database for the rate limit service. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
prometheus | RateLimitMetricsPrometheusProvider | true | Prometheus defines the configuration for prometheus endpoint. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
disable | boolean | true | Disable the Prometheus endpoint. |
RateLimitRedisSettings defines the configuration for connecting to redis database.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
url | string | true | URL of the Redis Database. | |
tls | RedisTLSSettings | false | TLS defines TLS configuration for connecting to redis database. |
RateLimitRule defines the semantics for matching attributes from the incoming requests, and setting limits for them.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
clientSelectors | RateLimitSelectCondition array | false | ClientSelectors holds the list of select conditions to select specific clients using attributes from the traffic flow. All individual select conditions must hold True for this rule and its limit to be applied. If no client selectors are specified, the rule applies to all traffic of the targeted Route. If the policy targets a Gateway, the rule applies to each Route of the Gateway. Please note that each Route has its own rate limit counters. For example, if a Gateway has two Routes, and the policy has a rule with limit 10rps, each Route will have its own 10rps limit. | |
limit | RateLimitValue | true | Limit holds the rate limit values. This limit is applied for traffic flows when the selectors compute to True, causing the request to be counted towards the limit. The limit is enforced and the request is ratelimited, i.e. a response with 429 HTTP status code is sent back to the client when the selected requests have reached the limit. | |
cost | RateLimitCost | false | Cost specifies the cost of requests and responses for the rule. This is optional and if not specified, the default behavior is to reduce the rate limit counters by 1 on the request path and do not reduce the rate limit counters on the response path. |
RateLimitSelectCondition specifies the attributes within the traffic flow that can be used to select a subset of clients to be ratelimited. All the individual conditions must hold True for the overall condition to hold True.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
headers | HeaderMatch array | false | Headers is a list of request headers to match. Multiple header values are ANDed together, meaning, a request MUST match all the specified headers. At least one of headers or sourceCIDR condition must be specified. | |
sourceCIDR | SourceMatch | false | SourceCIDR is the client IP Address range to match on. At least one of headers or sourceCIDR condition must be specified. |
RateLimitSpec defines the desired state of RateLimitSpec.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | RateLimitType | true | Type decides the scope for the RateLimits. Valid RateLimitType values are “Global” or “Local”. | |
global | GlobalRateLimit | false | Global defines global rate limit configuration. | |
local | LocalRateLimit | false | Local defines local rate limit configuration. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
metrics | RateLimitMetrics | true | Metrics defines metrics configuration for RateLimit. | |
tracing | RateLimitTracing | true | Tracing defines traces configuration for RateLimit. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
samplingRate | integer | false | SamplingRate controls the rate at which traffic will be selected for tracing if no prior sampling decision has been made. Defaults to 100, valid values [0-100]. 100 indicates 100% sampling. | |
provider | RateLimitTracingProvider | true | Provider defines the rateLimit tracing provider. Only OpenTelemetry is supported currently. |
RateLimitTracingProvider defines the tracing provider configuration of RateLimit
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | RateLimitTracingProviderType | true | Type defines the tracing provider type. Since to RateLimit Exporter currently using OpenTelemetry, only OpenTelemetry is supported | |
url | string | true | URL is the endpoint of the trace collector that supports the OTLP protocol |
Underlying type: string
Appears in:
Underlying type: string
RateLimitType specifies the types of RateLimiting.
Appears in:
| Value | Description |
|---|---|
Global | GlobalRateLimitType allows the rate limits to be applied across all Envoy proxy instances. |
Local | LocalRateLimitType allows the rate limits to be applied on a per Envoy proxy instance basis. |
Underlying type: string
RateLimitUnit specifies the intervals for setting rate limits. Valid RateLimitUnit values are “Second”, “Minute”, “Hour”, and “Day”.
Appears in:
| Value | Description |
|---|---|
Second | RateLimitUnitSecond specifies the rate limit interval to be 1 second. |
Minute | RateLimitUnitMinute specifies the rate limit interval to be 1 minute. |
Hour | RateLimitUnitHour specifies the rate limit interval to be 1 hour. |
Day | RateLimitUnitDay specifies the rate limit interval to be 1 day. |
RateLimitValue defines the limits for rate limiting.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
requests | integer | true | ||
unit | RateLimitUnit | true |
RedisTLSSettings defines the TLS configuration for connecting to redis database.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
certificateRef | SecretObjectReference | false | CertificateRef defines the client certificate reference for TLS connections. Currently only a Kubernetes Secret of type TLS is supported. |
RemoteJWKS defines how to fetch and cache JSON Web Key Sets (JWKS) from a remote HTTP/HTTPS endpoint.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. | |
uri | string | true | URI is the HTTPS URI to fetch the JWKS. Envoy’s system trust bundle is used to validate the server certificate. If a custom trust bundle is needed, it can be specified in a BackendTLSConfig resource and target the BackendRefs. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
pattern | string | true | Pattern matches a regular expression against the value of the HTTP Path.The regex string must adhere to the syntax documented in https://github.com/google/re2/wiki/Syntax. | |
substitution | string | true | Substitution is an expression that replaces the matched portion.The expression may include numbered capture groups that adhere to syntax documented in https://github.com/google/re2/wiki/Syntax. |
RequestHeaderCustomTag adds value from request header to each span.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | true | Name defines the name of the request header which to extract the value from. | |
defaultValue | string | false | DefaultValue defines the default value to use if the request header is not set. |
Underlying type: string
ResourceProviderType defines the types of custom resource providers supported by Envoy Gateway.
Appears in:
| Value | Description |
|---|---|
File | ResourceProviderTypeFile defines the “File” provider. |
ResponseOverride defines the configuration to override specific responses with a custom one.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
match | CustomResponseMatch | true | Match configuration. | |
response | CustomResponse | true | Response configuration. |
Underlying type: string
ResponseValueType defines the types of values for the response body supported by Envoy Gateway.
Appears in:
| Value | Description |
|---|---|
Inline | ResponseValueTypeInline defines the “Inline” response body type. |
ValueRef | ResponseValueTypeValueRef defines the “ValueRef” response body type. |
Retry defines the retry strategy to be applied.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
numRetries | integer | false | 2 | NumRetries is the number of retries to be attempted. Defaults to 2. |
retryOn | RetryOn | false | RetryOn specifies the retry trigger condition. If not specified, the default is to retry on connect-failure,refused-stream,unavailable,cancelled,retriable-status-codes(503). | |
perRetry | PerRetryPolicy | false | PerRetry is the retry policy to be applied per retry attempt. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
triggers | TriggerEnum array | false | Triggers specifies the retry trigger condition(Http/Grpc). | |
httpStatusCodes | HTTPStatus array | false | HttpStatusCodes specifies the http status codes to be retried. The retriable-status-codes trigger must also be configured for these status codes to trigger a retry. |
Underlying type: string
RoutingType defines the type of routing of this Envoy proxy.
Appears in:
| Value | Description |
|---|---|
Service | ServiceRoutingType is the RoutingType for Service Cluster IP routing. |
Endpoint | EndpointRoutingType is the RoutingType for Endpoint routing. |
SecurityPolicy allows the user to configure various security settings for a Gateway.
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
apiVersion | string | gateway.envoyproxy.io/v1alpha1 | ||
kind | string | SecurityPolicy | ||
metadata | ObjectMeta | true | Refer to Kubernetes API documentation for fields of metadata. | |
spec | SecurityPolicySpec | true | Spec defines the desired state of SecurityPolicy. | |
status | PolicyStatus | true | Status defines the current status of SecurityPolicy. |
SecurityPolicySpec defines the desired state of SecurityPolicy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
targetRef | LocalPolicyTargetReferenceWithSectionName | true | TargetRef is the name of the resource this policy is being attached to. This policy and the TargetRef MUST be in the same namespace for this Policy to have effect Deprecated: use targetRefs/targetSelectors instead | |
targetRefs | LocalPolicyTargetReferenceWithSectionName array | true | TargetRefs are the names of the Gateway resources this policy is being attached to. | |
targetSelectors | TargetSelector array | true | TargetSelectors allow targeting resources for this policy based on labels | |
apiKeyAuth | APIKeyAuth | false | APIKeyAuth defines the configuration for the API Key Authentication. | |
cors | CORS | false | CORS defines the configuration for Cross-Origin Resource Sharing (CORS). | |
basicAuth | BasicAuth | false | BasicAuth defines the configuration for the HTTP Basic Authentication. | |
jwt | JWT | false | JWT defines the configuration for JSON Web Token (JWT) authentication. | |
oidc | OIDC | false | OIDC defines the configuration for the OpenID Connect (OIDC) authentication. | |
extAuth | ExtAuth | false | ExtAuth defines the configuration for External Authorization. | |
authorization | Authorization | false | Authorization defines the authorization configuration. |
Underlying type: string
ServiceExternalTrafficPolicy describes how nodes distribute service traffic they receive on one of the Service’s “externally-facing” addresses (NodePorts, ExternalIPs, and LoadBalancer IPs.
Appears in:
| Value | Description |
|---|---|
Cluster | ServiceExternalTrafficPolicyCluster routes traffic to all endpoints. |
Local | ServiceExternalTrafficPolicyLocal preserves the source IP of the traffic by routing only to endpoints on the same node as the traffic was received on (dropping the traffic if there are no local endpoints). |
Underlying type: string
ServiceType string describes ingress methods for a service
Appears in:
| Value | Description |
|---|---|
ClusterIP | ServiceTypeClusterIP means a service will only be accessible inside the cluster, via the cluster IP. |
LoadBalancer | ServiceTypeLoadBalancer means a service will be exposed via an external load balancer (if the cloud provider supports it). |
NodePort | ServiceTypeNodePort means a service will be exposed on each Kubernetes Node at a static Port, common across all Nodes. |
Session defines settings related to TLS session management.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
resumption | SessionResumption | false | Resumption determines the proxy’s supported TLS session resumption option. By default, Envoy Gateway does not enable session resumption. Use sessionResumption to enable stateful and stateless session resumption. Users should consider security impacts of different resumption methods. Performance gains from resumption are diminished when Envoy proxy is deployed with more than one replica. |
SessionResumption defines supported tls session resumption methods and their associated configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
stateless | StatelessTLSSessionResumption | false | Stateless defines setting for stateless (session-ticket based) session resumption | |
stateful | StatefulTLSSessionResumption | false | Stateful defines setting for stateful (session-id based) session resumption |
ShutdownConfig defines configuration for graceful envoy shutdown process.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
drainTimeout | Duration | false | DrainTimeout defines the graceful drain timeout. This should be less than the pod’s terminationGracePeriodSeconds. If unspecified, defaults to 60 seconds. | |
minDrainDuration | Duration | false | MinDrainDuration defines the minimum drain duration allowing time for endpoint deprogramming to complete. If unspecified, defaults to 10 seconds. |
ShutdownManager defines the configuration for the shutdown manager.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
image | string | true | Image specifies the ShutdownManager container image to be used, instead of the default image. |
SlowStart defines the configuration related to the slow start load balancer policy.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
window | Duration | true | Window defines the duration of the warm up period for newly added host. During slow start window, traffic sent to the newly added hosts will gradually increase. Currently only supports linear growth of traffic. For additional details, see https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/cluster/v3/cluster.proto#config-cluster-v3-cluster-slowstartconfig |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | SourceMatchType | false | Exact | |
value | string | true | Value is the IP CIDR that represents the range of Source IP Addresses of the client. These could also be the intermediate addresses through which the request has flown through and is part of the X-Forwarded-For header.For example, 192.168.0.1/32, 192.168.0.0/24, 001:db8::/64. |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
Exact | SourceMatchExact All IP Addresses within the specified Source IP CIDR are treated as a single client selector and share the same rate limit bucket. |
Distinct | SourceMatchDistinct Each IP Address within the specified Source IP CIDR is treated as a distinct client selector and uses a separate rate limit bucket/counter. Note: This is only supported for Global Rate Limits. |
StatefulTLSSessionResumption defines the stateful (session-id based) type of TLS session resumption. Note: When Envoy Proxy is deployed with more than one replica, session caches are not synchronized between instances, possibly leading to resumption failures. Envoy does not re-validate client certificates upon session resumption. https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/route/v3/route_components.proto#config-route-v3-routematch-tlscontextmatchoptions
Appears in:
StatelessTLSSessionResumption defines the stateless (session-ticket based) type of TLS session resumption. Note: When Envoy Proxy is deployed with more than one replica, session ticket encryption keys are not synchronized between instances, possibly leading to resumption failures. In-memory session ticket encryption keys are rotated every 48 hours. https://www.envoyproxy.io/docs/envoy/latest/api-v3/extensions/transport_sockets/tls/v3/common.proto#extensions-transport-sockets-tls-v3-tlssessionticketkeys https://commondatastorage.googleapis.com/chromium-boringssl-docs/ssl.h.html#Session-tickets
Appears in:
StatusCodeMatch defines the configuration for matching a status code.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | StatusCodeValueType | true | Value | Type is the type of value. Valid values are Value and Range, default is Value. |
value | integer | false | Value contains the value of the status code. | |
range | StatusCodeRange | false | Range contains the range of status codes. |
StatusCodeRange defines the configuration for define a range of status codes.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
start | integer | true | Start of the range, including the start value. | |
end | integer | true | End of the range, including the end value. |
Underlying type: string
StatusCodeValueType defines the types of values for the status code match supported by Envoy Gateway.
Appears in:
| Value | Description |
|---|---|
Value | StatusCodeValueTypeValue defines the “Value” status code match type. |
Range | StatusCodeValueTypeRange defines the “Range” status code match type. |
StringMatch defines how to match any strings. This is a general purpose match condition that can be used by other EG APIs that need to match against a string.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | StringMatchType | false | Exact | Type specifies how to match against a string. |
value | string | true | Value specifies the string value that the match must have. |
Underlying type: string
StringMatchType specifies the semantics of how a string value should be compared. Valid MatchType values are “Exact”, “Prefix”, “Suffix”, “RegularExpression”.
Appears in:
| Value | Description |
|---|---|
Exact | StringMatchExact :the input string must match exactly the match value. |
Prefix | StringMatchPrefix :the input string must start with the match value. |
Suffix | StringMatchSuffix :the input string must end with the match value. |
RegularExpression | StringMatchRegularExpression :The input string must match the regular expression specified in the match value. The regex string must adhere to the syntax documented in https://github.com/google/re2/wiki/Syntax. |
TCPActiveHealthChecker defines the settings of tcp health check.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
send | ActiveHealthCheckPayload | false | Send defines the request payload. | |
receive | ActiveHealthCheckPayload | false | Receive defines the expected response payload. |
TCPClientTimeout only provides timeout configuration on the listener whose protocol is TCP or TLS.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
idleTimeout | Duration | false | IdleTimeout for a TCP connection. Idle time is defined as a period in which there are no bytes sent or received on either the upstream or downstream connection. Default: 1 hour. |
TCPKeepalive define the TCP Keepalive configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
probes | integer | false | The total number of unacknowledged probes to send before deciding the connection is dead. Defaults to 9. | |
idleTime | Duration | false | The duration a connection needs to be idle before keep-alive probes start being sent. The duration format is Defaults to 7200s. | |
interval | Duration | false | The duration between keep-alive probes. Defaults to 75s. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
connectTimeout | Duration | false | The timeout for network connection establishment, including TCP and TLS handshakes. Default: 10 seconds. |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
minVersion | TLSVersion | false | Min specifies the minimal TLS protocol version to allow. The default is TLS 1.2 if this is not specified. | |
maxVersion | TLSVersion | false | Max specifies the maximal TLS protocol version to allow The default is TLS 1.3 if this is not specified. | |
ciphers | string array | false | Ciphers specifies the set of cipher suites supported when negotiating TLS 1.0 - 1.2. This setting has no effect for TLS 1.3. In non-FIPS Envoy Proxy builds the default cipher list is: - [ECDHE-ECDSA-AES128-GCM-SHA256|ECDHE-ECDSA-CHACHA20-POLY1305] - [ECDHE-RSA-AES128-GCM-SHA256|ECDHE-RSA-CHACHA20-POLY1305] - ECDHE-ECDSA-AES256-GCM-SHA384 - ECDHE-RSA-AES256-GCM-SHA384 In builds using BoringSSL FIPS the default cipher list is: - ECDHE-ECDSA-AES128-GCM-SHA256 - ECDHE-RSA-AES128-GCM-SHA256 - ECDHE-ECDSA-AES256-GCM-SHA384 - ECDHE-RSA-AES256-GCM-SHA384 | |
ecdhCurves | string array | false | ECDHCurves specifies the set of supported ECDH curves. In non-FIPS Envoy Proxy builds the default curves are: - X25519 - P-256 In builds using BoringSSL FIPS the default curve is: - P-256 | |
signatureAlgorithms | string array | false | SignatureAlgorithms specifies which signature algorithms the listener should support. | |
alpnProtocols | ALPNProtocol array | false | ALPNProtocols supplies the list of ALPN protocols that should be exposed by the listener or used by the proxy to connect to the backend. Defaults: 1. HTTPS Routes: h2 and http/1.1 are enabled in listener context. 2. Other Routes: ALPN is disabled. 3. Backends: proxy uses the appropriate ALPN options for the backend protocol. When an empty list is provided, the ALPN TLS extension is disabled. Supported values are: - http/1.0 - http/1.1 - h2 |
Underlying type: string
TLSVersion specifies the TLS version
Appears in:
| Value | Description |
|---|---|
Auto | TLSAuto allows Envoy to choose the optimal TLS Version |
1.0 | TLS1.0 specifies TLS version 1.0 |
1.1 | TLS1.1 specifies TLS version 1.1 |
1.2 | TLSv1.2 specifies TLS version 1.2 |
1.3 | TLSv1.3 specifies TLS version 1.3 |
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
group | Group | true | gateway.networking.k8s.io | Group is the group that this selector targets. Defaults to gateway.networking.k8s.io |
kind | Kind | true | Kind is the resource kind that this selector targets. | |
matchLabels | object (keys:string, values:string) | true | MatchLabels are the set of label selectors for identifying the targeted resource |
Timeout defines configuration for timeouts related to connections.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
tcp | TCPTimeout | false | Timeout settings for TCP. | |
http | HTTPTimeout | false | Timeout settings for HTTP. |
TracingProvider defines the tracing provider configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
backendRef | BackendObjectReference | false | BackendRef references a Kubernetes object that represents the backend server to which the authorization request will be sent. Deprecated: Use BackendRefs instead. | |
backendRefs | BackendRef array | false | BackendRefs references a Kubernetes object that represents the backend server to which the authorization request will be sent. | |
backendSettings | ClusterSettings | false | BackendSettings holds configuration for managing the connection to the backend. | |
type | TracingProviderType | true | OpenTelemetry | Type defines the tracing provider type. |
host | string | false | Host define the provider service hostname. Deprecated: Use BackendRefs instead. | |
port | integer | false | 4317 | Port defines the port the provider service is exposed on. Deprecated: Use BackendRefs instead. |
zipkin | ZipkinTracingProvider | false | Zipkin defines the Zipkin tracing provider configuration |
Underlying type: string
Appears in:
| Value | Description |
|---|---|
OpenTelemetry | |
OpenTelemetry | |
Zipkin | |
Datadog |
Underlying type: string
TriggerEnum specifies the conditions that trigger retries.
Appears in:
| Value | Description |
|---|---|
5xx | The upstream server responds with any 5xx response code, or does not respond at all (disconnect/reset/read timeout). Includes connect-failure and refused-stream. |
gateway-error | The response is a gateway error (502,503 or 504). |
reset | The upstream server does not respond at all (disconnect/reset/read timeout.) |
connect-failure | Connection failure to the upstream server (connect timeout, etc.). (Included in 5xx) |
retriable-4xx | The upstream server responds with a retriable 4xx response code. Currently, the only response code in this category is 409. |
refused-stream | The upstream server resets the stream with a REFUSED_STREAM error code. |
retriable-status-codes | The upstream server responds with any response code matching one defined in the RetriableStatusCodes. |
cancelled | The gRPC status code in the response headers is “cancelled”. |
deadline-exceeded | The gRPC status code in the response headers is “deadline-exceeded”. |
internal | The gRPC status code in the response headers is “internal”. |
resource-exhausted | The gRPC status code in the response headers is “resource-exhausted”. |
unavailable | The gRPC status code in the response headers is “unavailable”. |
UnixSocket describes TCP/UDP unix domain socket address, corresponding to Envoy’s Pipe https://www.envoyproxy.io/docs/envoy/latest/api-v3/config/core/v3/address.proto#config-core-v3-pipe
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
path | string | true | Path defines the unix domain socket path of the backend endpoint. |
Wasm defines a Wasm extension.
Note: at the moment, Envoy Gateway does not support configuring Wasm runtime. v8 is used as the VM runtime for the Wasm extensions.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
name | string | false | Name is a unique name for this Wasm extension. It is used to identify the Wasm extension if multiple extensions are handled by the same vm_id and root_id. It’s also used for logging/debugging. If not specified, EG will generate a unique name for the Wasm extension. | |
rootID | string | true | RootID is a unique ID for a set of extensions in a VM which will share a RootContext and Contexts if applicable (e.g., an Wasm HttpFilter and an Wasm AccessLog). If left blank, all extensions with a blank root_id with the same vm_id will share Context(s). Note: RootID must match the root_id parameter used to register the Context in the Wasm code. | |
code | WasmCodeSource | true | Code is the Wasm code for the extension. | |
config | JSON | false | Config is the configuration for the Wasm extension. This configuration will be passed as a JSON string to the Wasm extension. | |
failOpen | boolean | false | false | FailOpen is a switch used to control the behavior when a fatal error occurs during the initialization or the execution of the Wasm extension. If FailOpen is set to true, the system bypasses the Wasm extension and allows the traffic to pass through. Otherwise, if it is set to false or not set (defaulting to false), the system blocks the traffic and returns an HTTP 5xx error. |
env | WasmEnv | false | Env configures the environment for the Wasm extension |
WasmCodeSource defines the source of the Wasm code.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
type | WasmCodeSourceType | true | Type is the type of the source of the Wasm code. Valid WasmCodeSourceType values are “HTTP” or “Image”. | |
http | HTTPWasmCodeSource | false | HTTP is the HTTP URL containing the Wasm code. Note that the HTTP server must be accessible from the Envoy proxy. | |
image | ImageWasmCodeSource | false | Image is the OCI image containing the Wasm code. Note that the image must be accessible from the Envoy Gateway. | |
pullPolicy | ImagePullPolicy | false | PullPolicy is the policy to use when pulling the Wasm module by either the HTTP or Image source. This field is only applicable when the SHA256 field is not set. If not specified, the default policy is IfNotPresent except for OCI images whose tag is latest. Note: EG does not update the Wasm module every time an Envoy proxy requests the Wasm module even if the pull policy is set to Always. It only updates the Wasm module when the EnvoyExtension resource version changes. |
Underlying type: string
WasmCodeSourceType specifies the types of sources for the Wasm code.
Appears in:
| Value | Description |
|---|---|
HTTP | HTTPWasmCodeSourceType allows the user to specify the Wasm code in an HTTP URL. |
Image | ImageWasmCodeSourceType allows the user to specify the Wasm code in an OCI image. |
WasmEnv defines the environment variables for the VM of a Wasm extension
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
hostKeys | string array | false | HostKeys is a list of keys for environment variables from the host envoy process that should be passed into the Wasm VM. This is useful for passing secrets to to Wasm extensions. |
Underlying type: string
WithUnderscoresAction configures the action to take when an HTTP header with underscores is encountered.
Appears in:
| Value | Description |
|---|---|
Allow | WithUnderscoresActionAllow allows headers with underscores to be passed through. |
RejectRequest | WithUnderscoresActionRejectRequest rejects the client request. HTTP/1 requests are rejected with the 400 status. HTTP/2 requests end with the stream reset. |
DropHeader | WithUnderscoresActionDropHeader drops the client header with name containing underscores. The header is dropped before the filter chain is invoked and as such filters will not see dropped headers. |
Underlying type: string
XDSTranslatorHook defines the types of hooks that an Envoy Gateway extension may support for the xds-translator
Appears in:
| Value | Description |
|---|---|
VirtualHost | |
Route | |
HTTPListener | |
Translation |
XDSTranslatorHooks contains all the pre and post hooks for the xds-translator runner.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
pre | XDSTranslatorHook array | true | ||
post | XDSTranslatorHook array | true |
Underlying type: string
XFCCCertData specifies the fields in the client certificate to be forwarded in the XFCC header.
Appears in:
| Value | Description |
|---|---|
Subject | XFCCCertDataSubject is the Subject field of the current client certificate. |
Cert | XFCCCertDataCert is the entire client certificate in URL encoded PEM format. |
Chain | XFCCCertDataChain is the entire client certificate chain (including the leaf certificate) in URL encoded PEM format. |
DNS | XFCCCertDataDNS is the DNS type Subject Alternative Name field of the current client certificate. |
URI | XFCCCertDataURI is the URI type Subject Alternative Name field of the current client certificate. |
Underlying type: string
XFCCForwardMode defines how XFCC header is handled by Envoy Proxy.
Appears in:
| Value | Description |
|---|---|
Sanitize | XFCCForwardModeSanitize removes the XFCC header from the request. This is the default mode. |
ForwardOnly | XFCCForwardModeForwardOnly forwards the XFCC header in the request if the client connection is mTLS. |
AppendForward | XFCCForwardModeAppendForward appends the client certificate information to the request’s XFCC header and forward it if the client connection is mTLS. |
SanitizeSet | XFCCForwardModeSanitizeSet resets the XFCC header with the client certificate information and forward it if the client connection is mTLS. The existing certificate information in the XFCC header is removed. |
AlwaysForwardOnly | XFCCForwardModeAlwaysForwardOnly always forwards the XFCC header in the request, regardless of whether the client connection is mTLS. |
XForwardedClientCert configures how Envoy Proxy handle the x-forwarded-client-cert (XFCC) HTTP header.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
mode | XFCCForwardMode | false | Mode defines how XFCC header is handled by Envoy Proxy. If not set, the default mode is Sanitize. | |
certDetailsToAdd | XFCCCertData array | false | CertDetailsToAdd specifies the fields in the client certificate to be forwarded in the XFCC header. Hash(the SHA 256 digest of the current client certificate) and By(the Subject Alternative Name) are always included if the client certificate is forwarded. This field is only applicable when the mode is set to AppendForward orSanitizeSet and the client connection is mTLS. |
XForwardedForSettings provides configuration for using X-Forwarded-For headers for determining the client IP address. Refer to https://www.envoyproxy.io/docs/envoy/latest/configuration/http/http_conn_man/headers#x-forwarded-for for more details.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
numTrustedHops | integer | false | NumTrustedHops controls the number of additional ingress proxy hops from the right side of XFF HTTP headers to trust when determining the origin client’s IP address. Only one of NumTrustedHops and TrustedCIDRs must be set. |
ZipkinTracingProvider defines the Zipkin tracing provider configuration.
Appears in:
| Field | Type | Required | Default | Description |
|---|---|---|---|---|
enable128BitTraceId | boolean | false | Enable128BitTraceID determines whether a 128bit trace id will be used when creating a new trace instance. If set to false, a 64bit trace id will be used. | |
disableSharedSpanContext | boolean | false | DisableSharedSpanContext determines whether the default Envoy behaviour of client and server spans sharing the same span context should be disabled. |
日期:2024 年 6 月 12 日
日期:2024 年 4 月 9 日
日期:2024 年 3 月 13 日
Type 和 required 的文档From 字段的支持